How To Prevent Business Email Compromise and Wire Fraud
Business Email Compromise (“BEC”) is one of the most pervasive cyber threats facing enterprises. In the FBI’s recently released Internet Crime Report (IC3) for 2018, BEC caused the greatest dollar losses of all reported internet crimes. Total losses from BEC have more than doubled since 2017 to over $1.2 billion, or about $63,000 per incident. This data is supported by claims from the cyber insurance carriers as well. According to a recent report by Beazley Breach Response, incidents that began with email compromise and resulted in fraudulent wires being sent, increased 133% year over year The proportion of cyber crimes handled by Beazely that involved BEC is now 24%, almost double the 13% share of the prior year.
How can companies protect themselves from this persistent threat? Our guide to preventing business email compromise and the resulting wire fraud, was designed by operating professionals with deep experience managing the financial controls of firms that moved tens of billions of dollars per year and were constantly targeted by criminals. We organized our guide into three key pillars of Business Email Compromise prevention and provided supporting ideas and best practices to stay safe.
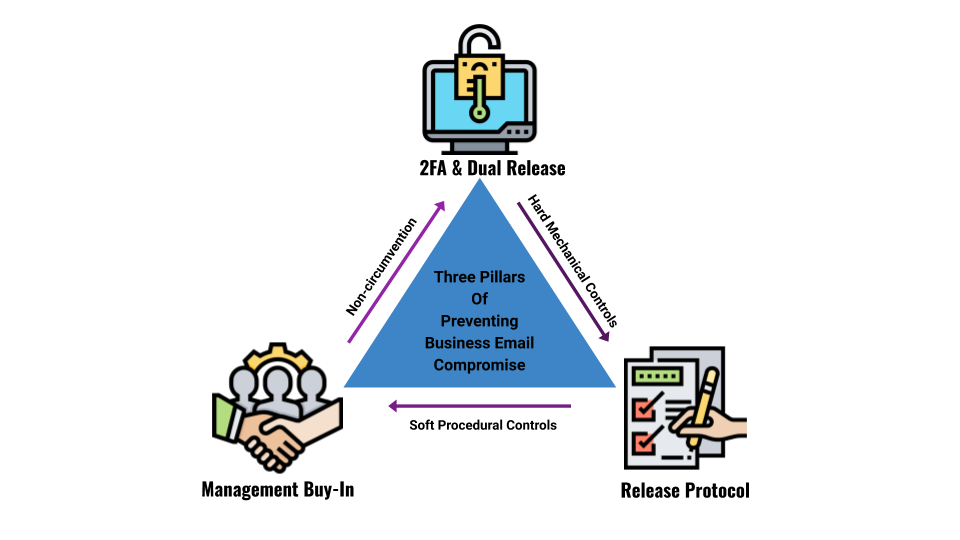
The Three Pillars of Business Email Compromise / Wire Fraud Prevention
Preventing BEC depends on Management Non-Circumvention, Hard access controls, and a strong internal process. When the work together, Business Email Compromise and its consequences can be avoided.
Pillar #1: Management Buy-In
The simple truth about preventing BEC is that management sets the tone. If management commits the following protocol and sets a consistent example, it will spread across the organization. If management circumvents protocol because they can’t be bothered, then BEC and wire fraud is likely to remain a risk. Given the cost of a single BEC incident, management buy-in would seem logical, but circumvention of the process is a common problem with financial operations controls. When an executive circumvents company protocol, it sends the signal that financial operations processes are merely suggestions, and can be used at an employees discretion. The discretionary application of financial controls is precisely the situation that cybercriminals take advantage of. If your organization’s management is not willing to practice what they preach then please skip to the end of this guide and read the section entitled “The bare minimum.”
Pillar #2: Two Factor Authentication and Dual Release
Dual Factor Authentication for bank login credentials and dual release controls for sending money out of a bank account are mandatory. Both create hard mechanical controls on bank access and permitted bank activity. There are no exceptions to these two requirements. They are the ONLY aspect of this program that is hard-wired and can’t be circumvented by breaking process.
Two Factor Authentication is critical to preventing Business Email Compromise
If your current commercial bank does not offer dual factor authentication via an authenticator application or an RSA token, then you need to switch banks. This may sound severe, but it is the truth. Preventing BEC requires a combination of both hard mechanical controls and soft procedural controls. 2FA should be an ‘All-or-None’ setting as well, meaning every employee has to use 2FA, no exceptions. If your bank can’t provide these hard mechanical controls, then your bank does not share your security concerns and is not aligned with your interests. Start bank shopping today if your bank does not offer this.
Dual Release controls on wires and ACHs is mandatory for preventing Business Email Compromise
Dual release controls prevent a single user from sending money. A standard dual release setup requires one authorized user to login and initiate the payment, and another user to log in separately to release the payment. Typically, the release must occur on the same business day it was created. The dual release is a powerful mechanical control as it prevents a single set of compromised credentials from sending money from an account. Two sets of compromised credentials would have to be stolen in order for a payment to be initiated and released. When combined with dual factor authentication the odds of compromise drop dramatically as both users would also have to be physically compromised (phone stolen and broken or RSA key stolen).
Role-based Access Controls Must Be Defined Well to Prevent Business Email Compromise
In addition to dual authentication and dual release, the banking platform you use should have strong role-based access controls that can only be modified by a master administrator, such as your CFO or CEO. The roles that the master admin creates empower members of the finance team to take certain actions. In general, only the master admin should have the ability to add or remove users and to change users roles. This prevents a lower level user from creating elevated user access, and possibly compromising the procedure. Additionally, only the master admin should have the ability to remove dual release controls or change any other company level security settings. Master Admins should take care to curate the roles carefully and always delete users from access should an employee leave the company. The HR department should have checkbox on ‘bank access removed’ for an employee departure checklist.
Additional Security Features That Your Bank Should Have
Your bank's notification suite should notify team members of any material changes (to roles, releases of wires or ACHs, new payees added, etc.). The finance team should all get alerts when payments are scheduled or sent. The more eyes on these alerts, the better chance an organization has to stop a compromise before damage is done. In addition to a strong notification suite, IP security settings can be a helpful layer of protection should an employee’s account become compromised. IP security settings restrict login access to a fixed list of IP addresses specified by the CFO or master administrator of the bank account. This means that wire requests and approvals are restricted to machines on the company’s physical network, or in a select subset of locations. This can be slightly inconvenient for teams that travel frequently but are a strong security feature to consider.
Pillar #3: IronClad Release Procedures
The soft controls in this section will cost the finance team an extra 45 seconds per transaction/approval. This is a negligible increase in processing time relative to the risk that it mitigates. It is important for all team members to recognize the value these controls yield.
Wire and ACH Release Procedures
Now that we have hard controls on both bank account access and permissions, it is time to build a process the finance team can follow every time a wire or ACH is sent.
Step 1: Create an internal only communication channel for members of the finance team that have the permission to initiate or release wires. The communications medium can either be an exclusive email or an internal chat application, like Slack. If email is used, an internal only distribution address should be created with JUST the members of the finance team on it. Note this should NOT be an actual email address that can send and receive emails from and to the outside world. Do NOT name it wires@yourcompany.com. It should be named something unique like pinkfloyd@yourcompany.com. This will guard against a cybercriminal trying to guess the email address and spoof a request.
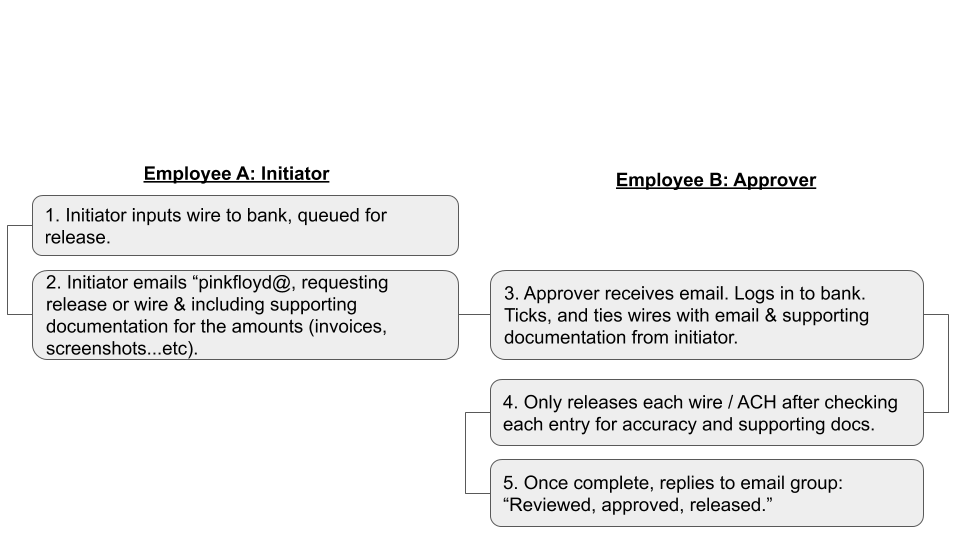
Step 2: Create a simple template for both initiating and releasing wires and ACH’s. The initiation of a wire or ACH should follow a step-by-step process by two parties empowered to login to the bank. For example:
When a wire or ACH needs to go out, the initiator logs into the bank and initiates the payment. The dual release control stops the release from going out immediately as it requires a second team member to log in to approve.
The initiator then emails pinkfloyd@yourcompany.com requesting release. The release request MUST include supporting collateral for the wire or ACH. Supporting collateral are things like physical invoices or payroll schedules. If supporting collateral is required for every request, the lack of supporting collateral will stick out if a spoofed email gets through. At a minimum, the second set of eyes will look at the spoofed email and hopefully question its authenticity.
The second employee that reviews the email then logs into the bank to review the request. They check the amounts versus the supporting collateral, and if it ties, can release the wire. They then respond the email confirming the release has gone out.
An example of what the correspondence on a typical release is below:
Typical thread to release a wire or ACH
The Bare Minimum: Pick up the Phone
If the three pillars we described can’t be implemented, a simple phone call between the party requesting payment and the finance team member can eliminate a lot of risks. Unless the requestor has been physically taken hostage or their persona and voice compromised, a spoofed email won’t survive phone verification. Call the person that sent the request and verify that their request is valid. If you suspect the person that answered the phone call has been compromised, suggest another method of communication or verification. For example, a verification question that only they would know can be asked (...where was our last off-site?). Either way, a verification phone call will eliminate a great deal of risk.
These BEC Controls Eliminate Most Common Risks Associated with Sending Money
Following the three pillars, we can tick off the threats that we’ve neutralized if we follow the process.
Spoofed Executive Email: If management does not circumvent the process, spoofed emails or phishing attempts will stick out like a sore thumb. Every team member will be able to differentiate between a legitimate request and a phishing attempt.
Email Compromise: If an email account is compromised and attempts to request a wire, the following safety measures stand in the way:
dual authentication on the bank login
wire request process would have to match, otherwise, the request would break protocol and stand out
dual release would prevent a single user from sending funds
strong notifications would tip the team off to an initiated wire that broke protocol.
Compromising an email account is not hard, but in order to break dual authenticatIon, physically compromising the employee’s phone or RSA token is necessary. This is highly unlikely.
Rogue or compromised employee: Let’s say an employee decides to steal from the company. That single rogue employee would still have to fabricate a great deal of supporting documentation in order to initiate a fake wire. They would also likely have to do so from the proximity of the company (if IP security is enabled), which makes getting caught quite risky.
Fat Finger Errors: This guide is focused on preventing business email compromise, but it has the added benefit of adding a second set of eyes to every transaction. This second set of eyes can help spot costly typing errors. Bonus!
Train, don’t Blame! Security Awareness Training Helps Prevent Business Email Compromise
Security awareness training on how to spot spoofed emails and phishing attempts should be part of EVERY company’s IT security program. Finance team members are frequently targeted by spear phishing campaigns given that their access to bank accounts. Regular monthly trainings and unannounced testing via products like Cofense should be mandatory. Blaming the employees is not the answer, build the right process and system so that even employee error won’t result in a loss.
What to Do If You Suspect Your Company Has Been the Victim of BEC
The MOMENT a person on the finance team suspects an outbound payment may have been fraudulent, the bank should be contacted and the wire department notified so that a stop order can be placed. The company should immediately contact law enforcement to report the crime. Unlike ransomware, where immutable bitcoin transactions are used, wires can be recalled and traced. Law enforcement has a good track record of recovering stolen funds that are a result of BEC. Once the dust settles, the company should do an exhaustive retrospective and analyze the circumstances that allowed the compromise to occur.