Ransom amounts rise 90% in Q1 as Ryuk increases
Coveware’s Q1 Ransomware Marketplace report aggregates anonymized ransomware data from cases handled and resolved by Coveware’s Incident Response Team. Unlike surveys, which rely on sentiment, this report is created solely from a standardized set of data collected from every case. By aggregating and sharing this data we believe large and small enterprises can better protect themselves from the persistent and ever-evolving ransomware threat. Please don’t hesitate to reach out to us with any questions or comments. Thank you for reading!
How Much Does a Ransomware Attack Cost?
The total cost of a ransomware attack can be divided into two main costs. First, the recovery cost. These expenses cover forensic reviews and assistance in rebuilding servers and work-stations. If a ransom is paid, then that is also a recovery expense. The second, and often more expensive cost of a ransomware attack is the total cost of downtime. Downtime costs are typically 5-10x the actual ransom amount and are measured in lost productivity (slack labor and lost revenue opportunities).
Ransom amounts paid daily during Q1 2019
In Q1 of 2019, the average ransom increased by 89% to $12,762, as compared to $6,733 in Q4 of 2018. The ransom increase reflects increased infections of more expensive types of ransomware such as Ryuk, Bitpaymer, and Iencrypt. These types of ransomware are predominantly used in bespoke targeted attacks on larger enterprise targets.
How Much Downtime Does a Ransomware Attack Cause?
In Q1 of 2019 average downtime increased to 7.3 days, from 6.2 days in Q4 of 2018. The increase in downtime was driven by the increased activity of ransomware that is difficult to decrypt, such as Ryuk. Similarly, the majority of the Hermes variants are also time-consuming to decrypt with relatively high data loss rates (10-20%) compared to other types of ransomware. Downtime increased by 47% over Q4. The increase in downtime was due to the frequency of attacks where backup systems were wiped or encrypted as part of the attack, an indicator of the increasingly bespoke nature of the attacks.
How Much Does Ransomware-related Downtime Cost?
In Q1, estimated downtime costs per ransomware attack per company averaged $65,645. The downtime costs become particularly acute for companies that lack cyber insurance and/or business interruption insurance. Downtime costs are estimated based on the geography and industry of the victim (to estimate labor costs), to estimate downtime costs per hour. Actual downtime costs may vary significantly from our estimates.
How Much Data Is Recovered After Paying a Ransom?
When a ransomware victim is forced to pay a ransom there are two success metrics that determine the outcome. First, does the payment result in a working decryption tool being delivered? If the threat actor did not deliver, it is considered a default and will likely lead to a 0% data recovery rate. Second, if a working decryption tool is delivered, how effective is it in decrypting the data? Files and servers can be damaged during or after the encryption process and this can affect data recovery rates even when a decryptor tool is delivered.
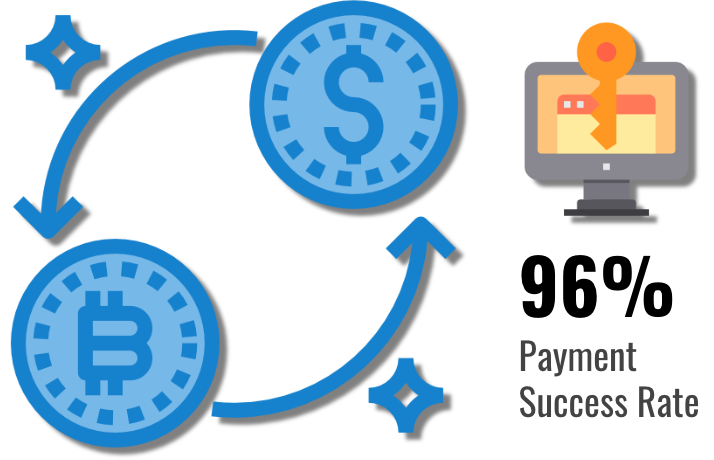
How Often Is a Decryption Tool Delivered After Paying a Ransom?
In Q1 of 2019, 96% of companies that paid the ransom received a working decryption tool. This was a 3% increase from the previous quarter. However, payment success rates varied depending upon the type of ransomware. For instance, the GandCrab TOR site remained very reliable and delivered a decryptor tool shortly after payment was executed. However, some variants of Dharma are much riskier depending on the variant and threat actor.
How Much Data Is Recovered with a Ransomware Decryptor?
In Q1 2019, victims who paid for a decryptor recovered 93% of the encrypted data. This statistic varied dramatically depending on the ransomware type. For example, Ryuk ransomware had a relatively low data recovery rate, at ~80%, while GandCrab was close to 100%. Data loss was due to an encryption process that damaged or wiped files, or inappropriate data modification to already encrypted files. Of course, sometimes the decryption tools are simply prone to error.
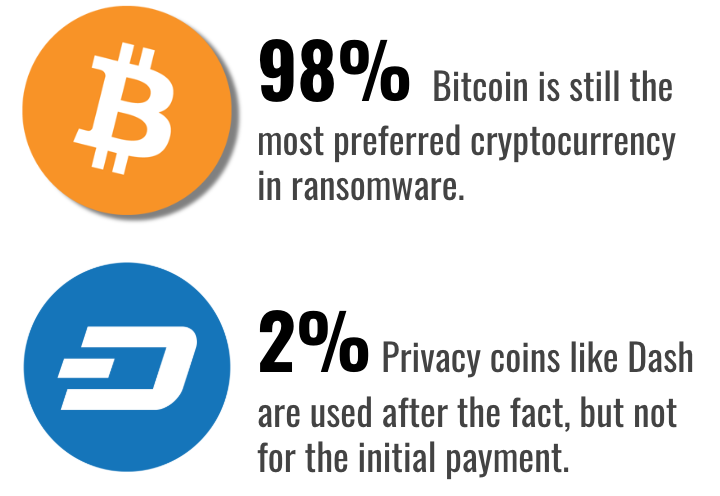
What Cryptocurrencies Are Used to Pay for Ransomware?
Bitcoin continues to be the most common cryptocurrency for ransomware payments and handling cryptocurrency continued to be a major source of friction for victims, and thus the threat actors as well. It is unlikely that ransomware rotates towards a different cryptocurrency anytime soon as they are even more nuanced to procure and handle. This is highlighted by the ease with which threat actors are ‘mixing’ bitcoin or exchanging them for other privacy coins, like Dash or Monero. Gandcrab is the only common type of ransomware that accepts payment in either Dash or Bitcoin. Gandcrab victims who pay with Bitcoin are charged 10% more due to the ‘mixing’ costs incurred by the threat actors to anonymize the bitcoin after payment.
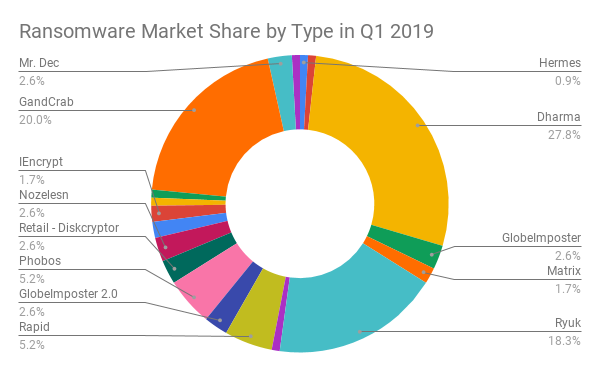
What Are the Most Common Types of Ransomware?
Dharma/Crysis continued to be the most prevalent ransomware in Q1 of 2019, but Ryuk gained significant market share (especially considering it was not in the top 3 in Q4 of 2018). The 3 most common types (Dharma, Ryuk, and GandCrab) are unique in their distribution methods, targets, and costs. Dharma continued to be operated by an increasing number of technically unsophisticated groups, which depressed data recovery rates despite rising ransom amounts. Ryuk continued to target larger enterprises and shock victims with egregious ransom demands. GandCrab continued to innovate distribution channels, with the developers bundling it with new and popular exploit kits.
What Were the Most Commonly Identified Attack Vectors for Ransomware?
Prior to a ransomware infection, multiple attack vectors may be used to gain access and/or control of a vulnerable system. Of those attack vectors, the most commonly identified continued to be Remote Desktop Protocol (RDP) based. However, email phishing was resurgent during Q1. We expect phishing-based attacks to increase in market share as social engineering techniques evolve and employee security awareness continues to be a hard problem to solve. Both RDP and phishing-based attacks have a primary goal of gaining elevated credentials. Once credentials are harvested the network can be surveilled, endpoint protection is sidestepped, backups are wiped/encrypted, and, finally, primary servers are encrypted.
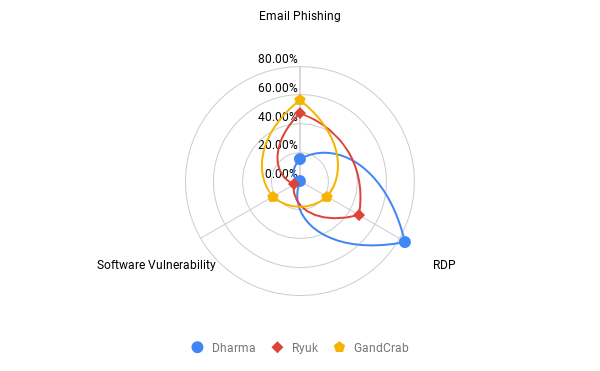
Comparing the Top Three Types of Ransomware by Attack Vector
The differences in the attack vector reflected the sophistication and preferences of the threat actors distributing the ransomware. Dharma continued to exploit exposed RDP ports, which are commonly found in smaller businesses. Ryuk relied much more on targeted email phishing, which reflects the threat actors preference to go after larger organizations. These more targeted attacks require more social engineering via spear and whale phishing techniques. GandCrab is one of the only ransomware types to utilize software vulnerabilities, the apex of which was the Connectwise/Kaseya exploit that impacted numerous managed service providers and their end clients during Q1 of 2019.
Comparing the Top Three Types of Ransomware by the Size of the Victim Company
The Q1 data paints a clear picture of Ryuk targeting larger organizations than Dharma and GandCrab. Ryuk was highly virulent in the midmarket and up during Q1, while Dharma variants continued to impact the midmarket and down. GandCrab’s impact was more scattered but tended to impact smaller companies and individual consumers.
Ryuk continued to set records with ransom demands that are an order of magnitude larger than other types of ransomware. Ryuk targeted larger organizations that have the financial capacity to pay larger demands and a lower tolerance for downtime. However, there is strong resistance forming to the size of these demands and we expect them to level off and as Ryuk seeks more targets down market.
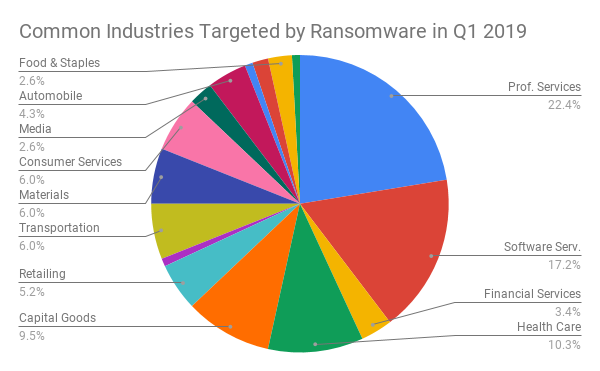
What Industries are Commonly Targeted by Ransomware?
Professional services, such as law firms and CPA firms, are very often targeted by ransomware. Small healthcare organizations, such as local specialist offices, are often targeted as well. These firms tend to under-invest in IT security and backup policies, and have a low tolerance for data loss, which makes them vulnerable ransomware targets.
What Was the Average Size of Company Targeted by Ransomware?
In Q1 of 2019, the average company size increased to 114 employees, up from 71 in Q4. This increase reflected an increased prevalence of ransomware types that target midmarket and large enterprise, like Ryuk and LockerGoga. The result of targeted phishing attacks, these infections were more common in Q1.
——————————-
Disclaimer:
Coveware is not responsible for any actions taken, errors or omissions (negligent or otherwise), regardless of the cause, or for the results obtained from the use of this content, or for the performance of any computer, hardware or software used or modified in conjunction with this content. The content is provided on an "as is" basis.
VIEWERS OF THIS REPORT AND ITS CONTENT DISCLAIM ANY AND ALL EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE OR USE, FREEDOM FROM BUGS, SOFTWARE ERRORS OR DEFECTS, THAT THE CONTENT'S FUNCTIONING WILL BE UNINTERRUPTED OR THAT THE CONTENT WILL OPERATE WITH ANY SOFTWARE OR HARDWARE CONFIGURATION.
In no event shall Coveware be liable to any party for any direct, indirect, incidental, exemplary, compensatory, punitive, special or consequential damages, costs, expenses, legal fees, or losses (including, without limitation, lost income or lost profits and opportunity costs or losses caused by negligence) in connection with any use of the content even if advised of the possibility of such damages.
Some images designed by ITIM2010 from Flaticon.