Dharma ransomware recovery rates fall as ransom demands skyrocket
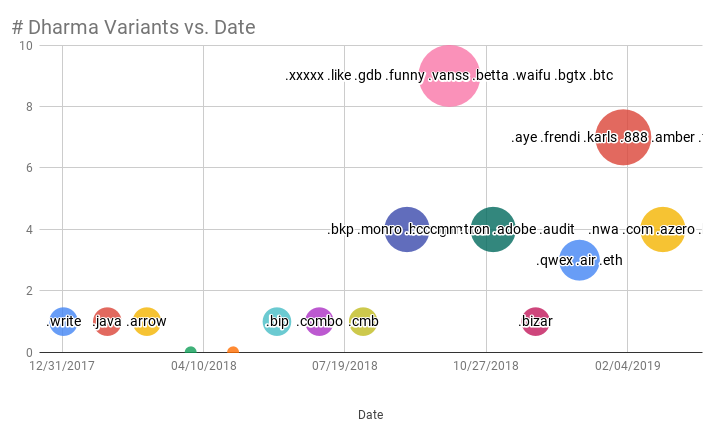
Last November, we wrote about the recent explosion in new variants of Dharma Ransomware. The proliferation of new Dharma variants indicated broader availability of the ransomware-as-a-service to new groups of affiliate distributors. At the time we noted that some of these new groups seemed less knowledgeable in their knowledge and operation of Dharma and its two step decryption process. Given those indicators we predicted an increase in bad outcomes for victims with no choice but to interact with the affiliate, pay the ransom, and run the decryption tool. Since November, the pace of new variant observation has plateaued, but the creation of new variants remains elevated as compared to a year ago.
Dharma Ransomware Recovery Rates Vary by Extension
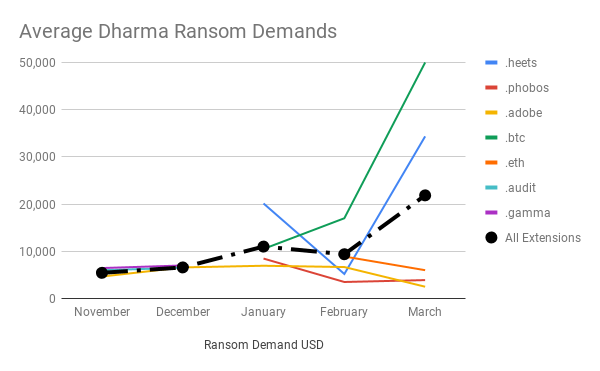
Our case data supports the thesis that as Dharma has gotten into the hands of less organized, less sophisticated groups, the data recovery rates of victims that end up paying has fallen. Variants controlled by less experienced groups create cases with lower average data recovery rates. Variants controlled by more experienced groups have higher data recovery rates. For example, the .heets extension has had a near 100% data recovery rate. Drilling down into the cases, we observed that the distributors have been selective in both the companies they target and the types of machines they encrypt. They are careful NOT to encrypt machines or file types that have a high risk of data corruption. Active SQL databases, for instance, can be especially fragile when it comes to encryption, and the loss of a SQL DB can materially impact the recovery of a victim company. The .heets operators seem to understand this and only target machines, file types and databases that they are confident will decrypt cleanly. This behavior is indicative of maturity, as the group acts rationally from an economic perspective showing great care for their reputation. In a sense, they care that the victim can recover their data.
Certain Dharma Variants are Developing a Negative Reputation
On the other end of the spectrum, variants such as .adobe are seeing a decline in data recovery rates because some distributors either don’t know or don’t care enough to be selective in how they encrypt a victim’s data. The end result is and increase of cases with poor data recovery rates. The lost data leads to a reluctance of future victims to consider payment as a viable recovery option (note, paying a ransom should ALWAYS be the option of last resort). Current and future victims are rightly served to understand these risks before traveling down the path of last resort to recover their data. Victims of any type of ransomware should be aware of these risks, and seek counsel before even considering payment as a viable option for recovery.
With Dharma You Get What You Pay For… Sometimes
While average data recovery rates for Dharma have been falling, average ransom demands have been skyrocketing. The average ransom demand has doubled twice since November. However, the distribution of ransom demands by variant explains a lot of the increase. Certain variants, like .heets, have on generally targeted larger networks, possibly a sign of sophistication and maturity of the group distributing it. Other variants like .eth, .phobos and .adobe have remained relatively flat, as they continue to target smaller organizations that remain exposed via common attack vectors and vulnerabilities.
Distributors May Be Shifting Away from Dharma to More Efficient Types of Ransomware-As-A-Service
The Dharma two-step decryptor is an effective control mechanism that allows the developers to moderate the flow of decryption keys. It is also a logistical nightmare for victims and, by extension, the ransomware distributors. We have observed the rise in popularity of GandCrab and other more simple types of encryption ransomware. GandCrab has standardized ransom payments through their TOR site, which dramatically decreases support costs for distributors. It is also widely packaged in several prevalent exploit kits. We have also observed ransom attacks using off the shelf encryption software. These shifting tastes towards efficiency and simplicity, have been further exemplified by an increasing number of Mr. Dec Ransomware infections. While not particularly prevalent, Mr. Dec has been showing up more frequently of late. Interestingly, the demand notes and communications of several Mr Dec groups are almost 100% overlapping with certain variants of Dharma, suggesting that prior Dharma groups have abandoned the hassle of the Dharma two-step decryptor in favor of Mr Dec, (which has a one step decryptor by unique ID), and have taken their ransom note and demand email templates with them.
Avoid Falling Victim to Dharma and Other Types of Active Ransomware
With ransom demands skyrocketing and recovery rates falling, the attack patterns and vectors continues to be consistent. Exposed RDP continues to be the primary attack vector. However, don’t disregard the sophistication of recent email phishing campaigns.Today’s malicious emails frequently carry a payload that serves as an initial point of ingress to monitor and eventually harvest login credentials. If domain admin credentials are compromised, lateral movement throughout the network allows attackers to surveil the network topography before disabling AV & Endpoint protection and deploying encryption executables across primary and backup systems.
A layered approach to both hard and soft security measures is necessary to defend against these types of attacks. Security awareness training can decrease the likelihood of employees clicking on malicious links. Least privilege principle can prevent harvested credentials from enabling broad lateral access. Strong 2FA on admin accounts, along with properly partitioned backups can prevent even compromised credentials from causing a catastrophe.