Cr1ptT0r Ransomware Targets NAS Devices with Old Firmware
New Strain of Ransomware: Cr1ptT0r Virus Targets NAS Devices with Old Firmware
In late February a new type of ransomware emerged that targeted a very narrow set of vulnerabilities on a very common piece of storage hardware, NAS devices. The ransomware, branded Cr1ptT0r, targeted NAS devices commonly used as extra network drives and also as backups (not recommended!).
While it is common for NAS devices to get swept up in a ransomware attack, Cr1ptT0r is unique in that the distributors have limited their attacks to just NAS devices. The distribution strategy stands in stark contrast to broadly distributed ransomware like GandCrab, where the developers appear to be focused on becoming the most prevalent strain of ransomware.
How Cr1ptT0r Ransomware Spreads
Mass port scanning for internet connected NAS devices is a commodity activity, so finding open targets for Cr1ptT0r is fertile hunting for ransomware distributors. Additionally, the firmware of certain NAS devices are not updated frequently, and many active devices are no longer supported by their manufacturer. The large base of devices with unpatched vulnerabilities makes them a niche, yet ripe target for attack.
How Cr1ptT0r Ransomware Encrypts Your Files
After finding an unpatched, internet connected device, Cr1ptT0r is deployed and encryption set in motion. In our conversations with Cr1ptT0r ransomware chat support, they revealed that one particular NAS manufacturer had a hidden folder in the device that is used for add ons. The folder is either “Volume_1/Nas_Prog” or “/mnt/HD/HD_a2/Nas_Prog”. It is here that the malicious executable in a folder called “cr1ppt0r” was planted.
If the executable is allowed to complete, the device’s data is fully encrypted starting with the smallest files. The priority of encryption is meant to ensure a large number of files are encrypted before anyone notices.
By contrast, most branded ransomware only partially encrypt files. Partial encryption enables the ransomware to affect large networks at high velocity in the hope that no person or system notices until it’s too late. Cr1ptT0r, on the other hand, fully encrypts every file which makes the decryption process time consuming and resource intensive. The lengthy encryption process provides victims a window to notice the process and halt it.
After fully encrypting a device, the ransomware leaves behind two files, a ransom note and a text file of the Cr1ptT0r logs called “_cr1ptt0r_logs.txt.”
How to Remove Cr1ptT0r Ransomware & Recover Data
If you are affected by Cr1ptT0r, at a minimum you should backup the data, format the drive and update the device. Victims should not leave NAS devices open to the internet. Also, it should be noted that NAS devices that are not properly partitioned should not be used as backup devices. If there are no other options for recovering your data, paying the ransom should be the absolute last option.
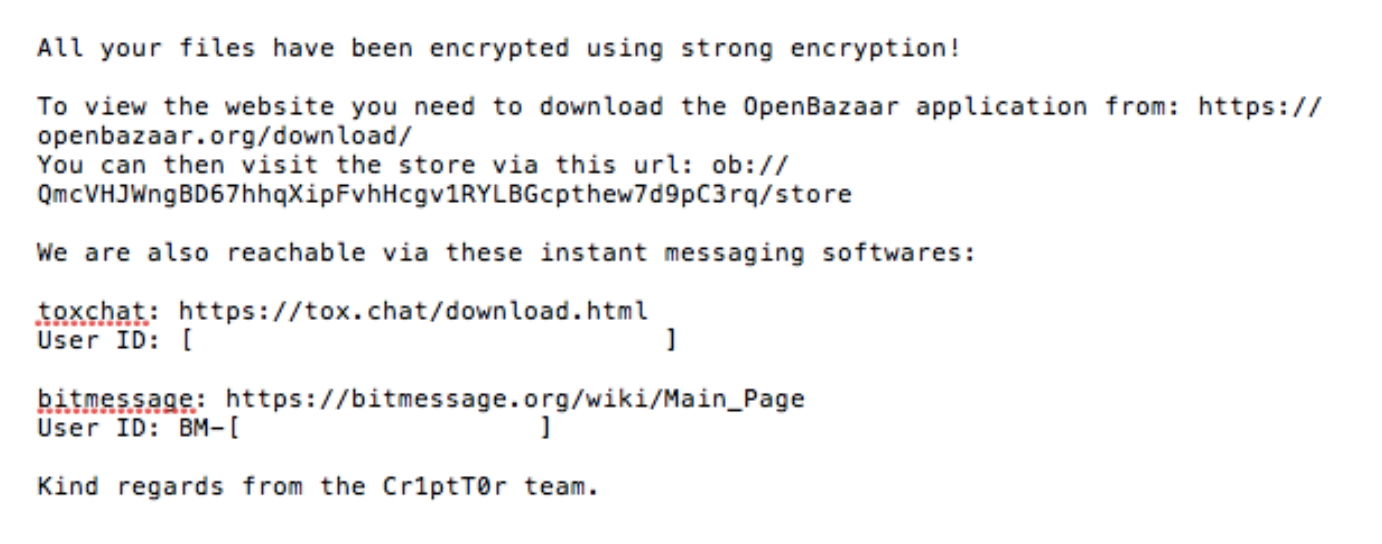
The standard ransom note for Cr1ptT0r directs the victim to either visit an OpenBazaar page, or to send a message to the ransomware support team via ToxChat or Bitmessage.
The Cr1ptT0r team does not seem interested in scaling their ransom demands based on the perceived size of the company, amount of encrypted data, or urgency of the victim. Rather, decryption keys are sold at a fixed cost for an entire device, or à la carte per file.
This is yet another way that the Cr1ptT0r strategy differs from other types of ransomware. Time spent negotiating with victims can be time-consuming and costly for ransomware distribution campaigns. Rather than burn support hours, the Cr1pT0r distributors have priced decryption at the low end of the average ransom amount ($1,200). Below is an image of the standard Cr1ptT0r ransom note.
Each victim's public key is also at the top of their “_cr1ptt0r_logs.txt” file. When speaking with the developer over chat, they will note the victims public key for reference.
How to Decrypt Files Encrypted by Cr1ptT0r Ransomware after Receiving a Private Key
If a victim chooses to pay the ransom, the chat operator will ascertain the encrypted device type and firmware version. Once a private key is acquired, the steps are relatively straightforward but can vary based on device type and firmware. For standard devices, such as a DNS-320 running FW version 1.03, the process is:
Rename current _cr1ptt0r_logs.txt so that it does not interfere with a new log file being created
Upload _cr1ptt0r_privkey.txt to the root, which is the same folder that the _cr1ptt0r_logs.txt gets saved to
Reboot the device
For different device manufacturers, the Cr1ptT0r operator may provide a script that needs to be run, vs just a file that needs to be saved to the root. There is no screen or application window to view during the decryption process like other types of ransomware. The only way to monitor decryption progress is to look at the _cr1ptt0r_logs.txt file. Once complete, the word "done" will be the last line of the log file.
The decryption process can take a long time because every file is fully encrypted. Similarly, connecting to the device during decryption may be difficult because of how resource intensive the process is. The Cr1ptT0r operator can provide faster decryption options, but it requires the victim to mount the drive on a linux system. If the victim is able to do this, then the Cr1ptT0r support team can provide a binary for linux x86 or x64 that will decrypt the device faster.
Finally, victims should not assume that they should do a firmware update when a device becomes encrypted. Running updates while the device is still encrypted can complicate the decryption process.
Comparing Cr1ptT0r Ransomware to GandCrab Ransomware
When assisting victims of Cr1ptT0r, the similarities and differences with other types of ransomware are clear. All are criminal, but noting the differences paints a clear picture of the personality and ambitions of the developers and operators behind them.
For example, GandCrab clearly has global ambitions to become the ransomware type of choice for affiliate distribution and exploit kits. Compared to Cr1pT0r, GandCrab has broader distribution (more companies hit) and scope (more data/storage encrypted devices in each attack). GandCrab is taking a move fast and break things approach, even if it means overwhelming their TOR site operators while distribution is scaled.
The developers of Cr1ptT0r are taking the opposite tack, constraining distribution to a single device type, standardizing the extortion payment process (fixed prices for a device, or a file), and keeping the decryption simple to minimize their support costs.
When considering these two type of ransomware as businesses, it is clear that Cr1ptT0r has opted for simplicity; they are targeting a higher victim conversion rate via low-cost ransom and simple of decryption. Contrariwise, GandCrab, with its recent inclusion in Trickbot exploit kits and role in the recent Kaseya / Connectwise vulnerability, is taking the exact opposite approach.
How To Protect Your Business from Cr1ptT0r Ransomware Virus
NAS devices should never be directly exposed to the internet. If a NAS device requires a connection from outside the network, companies should take the necessary precautions to ensure that connection is secured through multiple layers. RDP continues to be a prime attack vector for ransomware, so any company allowing access to a NAS through RDP should be aware of the risks and take necessary precautions. These include, but are not limited to:
Changing the default port setting on RDP from 3389
Whitelisting ONLY the IP addresses the need access
Setting a lockout on login attempts to prevent brute forcing
Requiring that access be established over a VPN
Requiring 2FA to access the NAS via RDP.
Cr1ptT0r Ransomware Downtime and Cost
Because Cr1ptT0r does not completely cripple every server and machine inside an organization, it is unlikely that an attack would create severe downtime costs. NAS devices are principally used as supplemental storage venues, or backups (note: we strongly advise against using a single NAS device as your primary backup option), so the loss of access is more of a business hindrance than a business blocker. If a victim must pay for a decryption key, we also note that the fixed cost (currently $1,200 per device) is substantially lower than the average Dharma or Ryuk ransomware cost.
Contact us if you are in need of immediate assistance.