Matrix Ransomware Recovery, Payment & Decryption Statistics
The information below describes relevant statistics of Matrix ransomware recovery, payment and decryption. The recovery process of Matrix ransomware includes identifying the strain and the risk associated with pursuing a ransom payment for data decryption. Please review the information below, or contact our support team, to learn more about Matrix ransomware recovery, payment and decryption statistics.
HOW MUCH ARE MATRIX RANSOMWARE RANSOM DEMANDS?
Matrix ransomware payments are typically lower than the ransomware marketplace average. Matrix affects small to mid-sized sized organizations that have lower ability to pay relative to larger businesses.
MATRIX RANSOMWARE: RANSOM AMOUNTS
Average Matrix Ransom Payment (November 2021)
HOW LONG DOES IT TAKE TO RECOVER FROM A MATRIX RANSOMWARE ATTACK?
Matrix Ransomware incidents are generally shorter than other types of ransomware due to the efficiency of the decryption process.
Immediate MATRIX Ransomware Help
For immediate assistance contact us
What else do I need to know?
Decrypting Matrix Ransomware
Matrix is different than other forms of ransomware because it changes the name of the entire file, instead of appending a unique value at the end of each file name
Each drive or local disk will contain a distinct unique ID that is shown in all of the file names. You must search the entire network to ensure that all IDs have been found and cataloged.
The attacker will need a copy of each file with a unique ID to begin generating the decryptor tool.
Steps to Run Matrix Decryption Tool
Remove Malware: Run your standard AV on each affected machine and clean off the ransomware executable. Most AV software should find the executable. If you not found by AV, you can run the following test:
Take a clean unencrypted test file, save it to a blank USB
Plug the USB into the infected machine
Boot the machine
If the test file on the USB gets encrypted, the malware is still there...keep searching
If the test file does not get encrypted. Your machine should be safe to proceed.
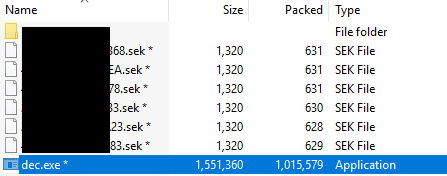
Run Decryptor: After paying the ransom, you will be sent a .zip file with the decryptor application and several .sek file. Download onto affected machine. The folder will typically look like below:
1. Ensure that all AV is removed or turned off. AV will keep the decryptor from running as intended.
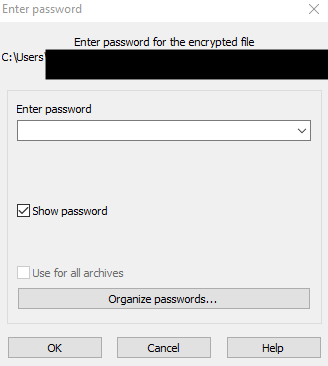
2. Run as administrator. The tool will first request a password, if the threat actor has enabled this feature.
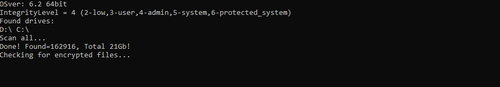
3. The tool will then search the system for encrypted files.
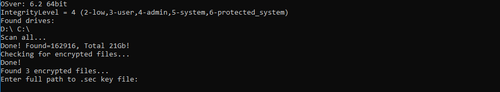
4. Once the Tool finds all encrypted files, it may require a path to be outlined for each .sek file. If you are scanning the entire network but have multiple .sek files, you’ll need to run the tool once for every distinct .sek file. This process may be time consuming depending on the number files.
If the attacker has provided a README file that outlines which ID corresponds to each .sek file, then you may be able to scan only the desired drive and provide the path to the corresponding .sek file.
5. After entering the .sek file path, the tool will automatically begin decrypting the files that are associated with the .sek file. As the files decrypt, they will automatically revert to their original file names.
6. After running the tool for a specific .sek file, a summary report will show the files that were not decrypted. If you’re scanning the entire network, then expect the report to show (i) files that cannot be opened and were likely never decrypted in the first place and (ii) invalid RSA messages for files that are not correlated to the specific .sek file. Files that are successfully decrypted will not appear in the report.
If all files were successfully decrypted, then you will no longer see any invalid RSA messages.
matrix RANSOMWARE FREQUENTLY ASKED QUESTIONS
1. ARE THERE FREE Matrix DECRYPTION TOOLS?
The majority of active Matrix ransomware variants can not be decrypted by any free tool or software. If you submit a file example to us, we will have a look for free and let you know. There are also good free websites that you can upload a sample file to and independently check. You should NOT pay a data recovery firm or any other service provider to research your file encryption. They will use the same free resources noted above… so don’t waste your money or time!
2. HOW DID I GET INFECTED WITH MATRIX RANSOMWARE?
Most Matrix ransomware is laid directly by a hacker that has accessed an unprotected RDP port, utilized email phishing to remote into a network via an employee’s computer, or utilized malicious attachments, downloads, application patch exploits or vulnerabilities to gain access to a network.
3. WHAT ARE RECENT MATRIX RANSOMWARE FILE EXTENSIONS?
Since Matrix changes the entire file name to a unique ID, it is hard to tell if an encrypted file has been impacted by Matrix.
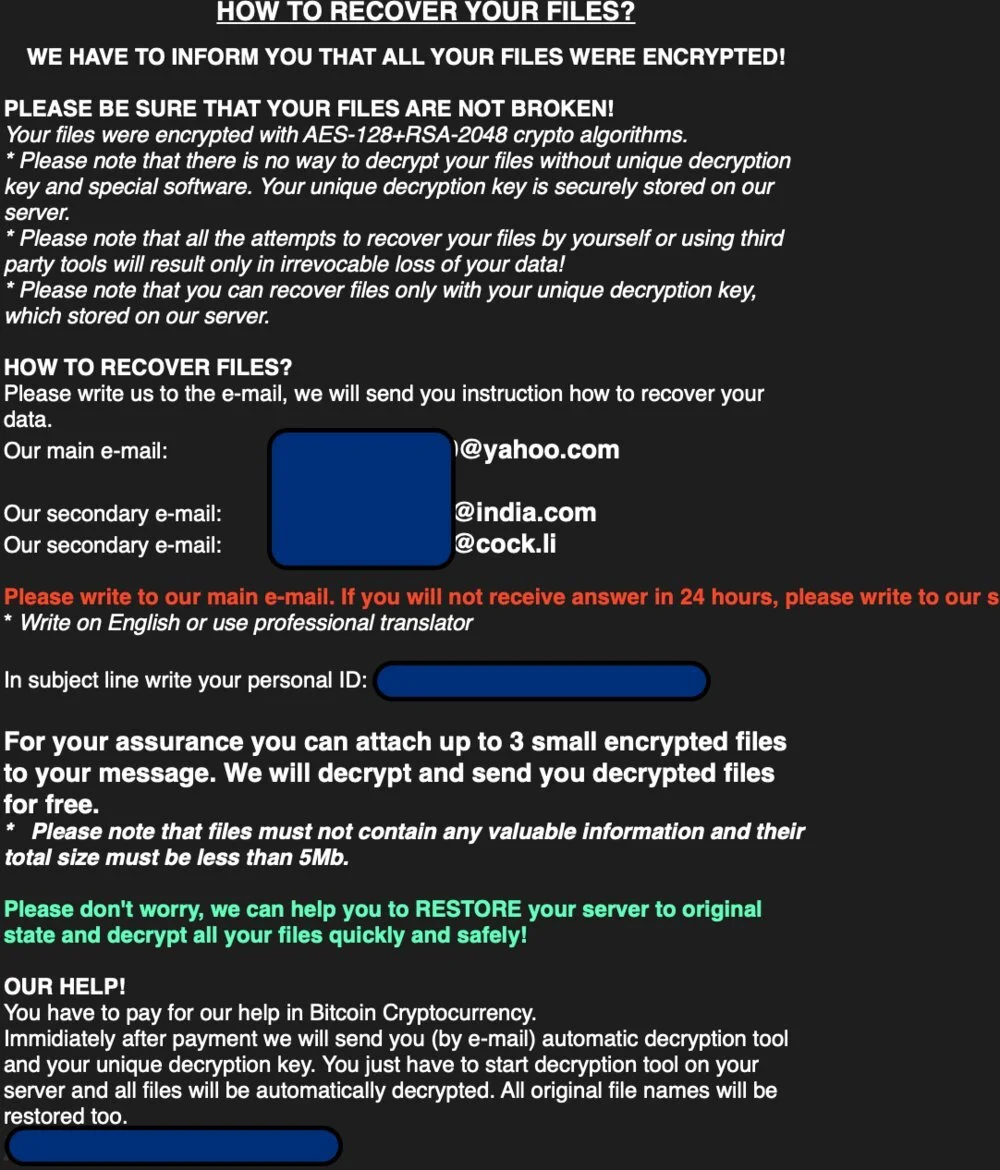
4. WHAT DOES A MATRIX RANSOM NOTICE LOOK LIKE?
Matrix ransomware hackers will leave a .txt or .rtf file notice behind that will be prominent and easy to find. It commonly looks like like the image below.
Note: We do not advise that any person or company contact a hacker and negotiate directly. Cyber criminals can be difficult to communicate with. Let a professional assist you.
Example Matrix ransom notice .txt file
RANSOMWARE FREQUENTLY ASKED QUESTIONS
WHAT INFORMATION DO I NEED TO PROVIDE?
You will need to provide information from both the ransom notice and a sample encrypted file. We will schedule a call to discuss the severity of the attack, the operability of your company and the likely timeline / cost of recovering from the attack. You will also need to provide identifying information on your company, and an authorized representative of your company.
HOW MUCH WILL THIS COST?
You are already being extorted; we don’t think you deserve to pay another large fee. Coveware charges flat per incident fees. Whether the case lasts one week or three weeks, our fees are flat. We do not charge spreads of fees tied to the size of the ransom amount. Our fees will never be even close to the amount of the ransom demanded by the cyber criminal, and you should be skeptical of why any other service provider would charge a fee that high.
WHAT ABOUT FIRMS THAT HAVE TOLD ME THEY CAN DECRYPT MY FILES WITHOUT PAYING THE HACKER?
You should be extremely skeptical of any data recovery firm that claims they can decrypt ransomware. Typically they are just paying the cyber criminal without your knowledge and pocketing the difference between the ransom amount and what they will charge you. Know the facts before you engage. If the ransomware IS decryptable, the tool can be found for free. If not, purchasing a key from the cyber criminal is the only way to unlock your files. While Coveware does not condone paying cyber criminals, we recognize it is often the only choice if backups are not available or have become compromised as well. If that is the case, you deserve an honest, transparent experience.
WILL THE RANSOMWARE PAYMENT BE SUCCESSFUL?
There is no guarantee that paying the ransom will result in a working decryption tool being delivered. However, Coveware believes that data aggregation can help customers make the most informed data-driven decisions. Since we handle lots of cases of the same ransomware types, we are able to share our experiences and help customers decide how to proceed.
HOW DO I UNLOCK MY FILES?
If the ransomware payment is successful, a decryption tool & key is provided by the hacker that can be used to manually decrypt your files.
HOW DO I PREVENT THIS FROM HAPPENING AGAIN?
There are some common security mis-configurations that lead to a ransomware attack. We can share some tips and resources for preventing future attacks, but encourage companies to perform a full forensic review or security assessment as soon as possible. Consistent investment in security IT is the best antidote to preventing future attacks.
WHY CHOOSE COVEWARE RANSOMWARE RECOVERY SERVICES?
FREE
RANSOMWARE ASSESSMENT
Provide a few details from the ransom notice, an example encrypted file and details of the operability of your company and budget/time. We will provide context into the severity of the attack and your options for decryption and recovery using our database of similar cases.
Identify ransomware type
Find free decryptor tools
Identify threat actor group
24x7 SUPPORT
- RANSOMWARE INCIDENT RESPONSE
We have deep experience communicating and negotiating with hackers. It’s what we do all day long! Take advantage of our experience and allow us to shoulder this burden.
Secure & safe negotiations
Proactive service
Transparent communications
Determine risks & outcomes
FILE DECRYPTION
& RECOVERY SUPPORT
Coveware has access to a ready supply of any crypto currency, and offers a 15 minute disbursement service level agreement. We also support the decryption/data recovery process.
Professional IT support
Insurance documentation
Post-incident follow up
Post-incident support
How does Coveware help our partners?
* Source: CDNet