Dharma Ransomware Recovery, Payment & Decryption Statistics
The information below describes relevant statistics of Dharma ransomware recovery, payment and decryption. The recovery process of Dharma ransomware includes identifying the strain and the risk associated with pursuing a ransom payment for data decryption. Please review the information below, or contact our support team, to learn more about Dharma ransomware recovery, payment and decryption statistics.
HOW MUCH ARE DHARMA RANSOMWARE RANSOM DEMANDS?
Dharma ransomware payments are lower than the ransomware marketplace average. This is due to the bespoke nature of the attacks and also the manual syndication of ransom payment collection that most Dharma hackers employ. Dharma is known for its widespread attacks on small businesses.
DHARMA RANSOMWARE: RANSOM AMOUNTS
Average Dharma Ransom Payment (June 2022)
HOW LONG DOES IT TAKE TO RECOVER FROM A DHARMA RANSOMWARE ATTACK?
Dharma ransomware incidents can be burdensome due to the complicated nature of the decryption tool provided by hackers. However, the recovery period is lower than the average since this group targets small networks that can be remediated quickly, as opposed to larger networks.
HOW DOES DHARMA RANSOMWARE ATTACK A VICTIM?
The majority of Dharma Ransomware attacks can be traced back to Remote Desktop Protocol access as the attack vector. This is due to the prevalence of poorly secured RDP ports, and the ease with which Ransomware distributors are able to either brute force themselves, or purchase credentials on dark market sites. Companies that allow employees or contractors to access their networks through remote access without taking the proper protections are at a grave risk of being attacked by Dharma Ransomware.
Immediate Dharma Ransomware Help
Due to the more targeted nature of Dharma ransomware, recovery efforts are usually more time consuming than average.
For immediate assistance contact
How to Identify Dharma Ransomware
Dharma Ransomware typically leaves behind a ransom note in 3 different formats; a multicolored Ransom Note, a simple text file ransom note, or no ransom note at all.
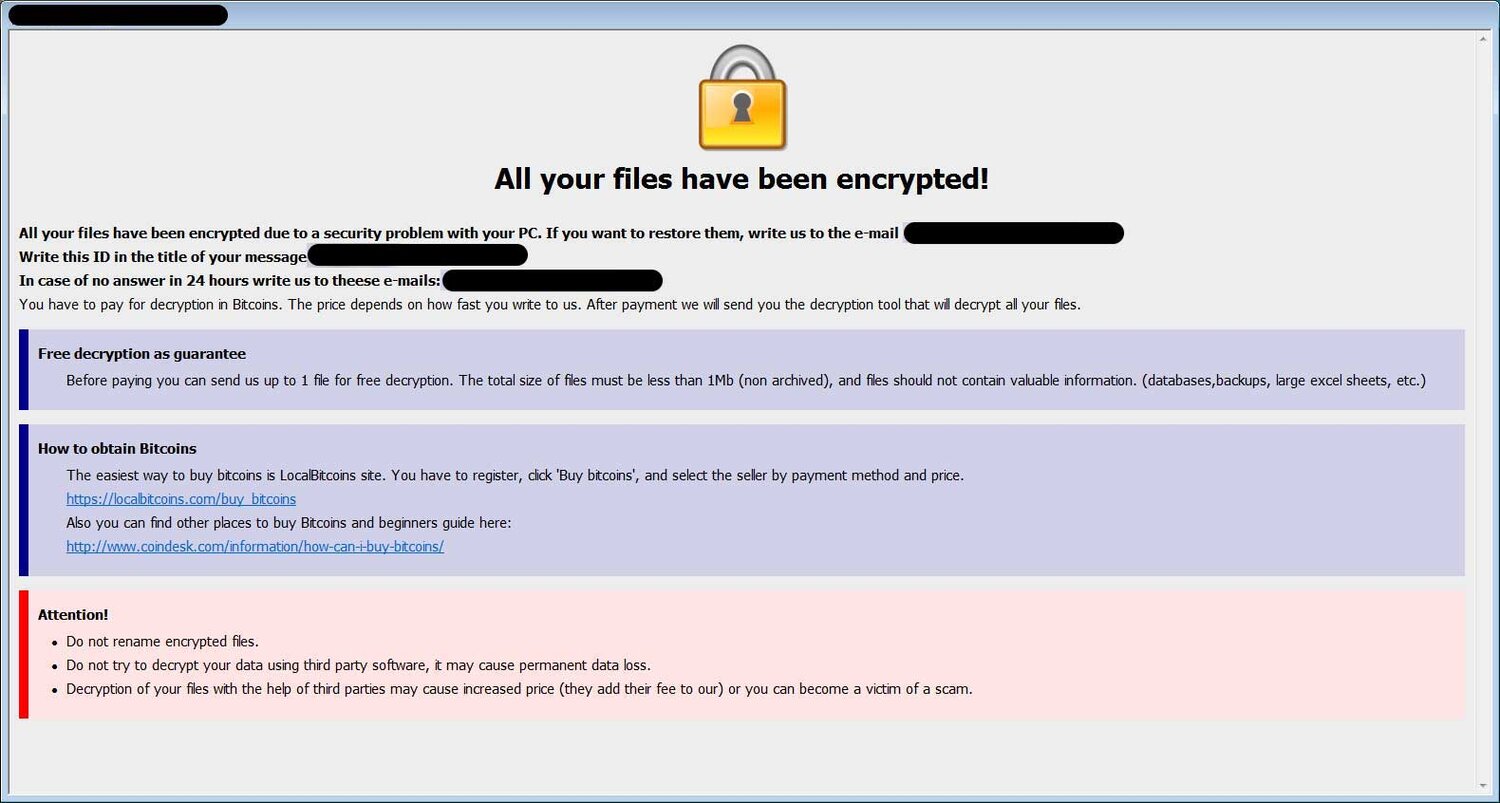
DHARMA RANSOMWARE NOTE #1: MULTICOLORED
The standard format and layout of a Dharma Ransomware Ransom Note
DHARMA RANSOMWARE NOTE #1: COLORED DHARMA RANSOM NOTE
The most common Dharma Ransom note is multicolored and contains 4 main sections.
Instructions:
At the top of the ransom note, the victim is provided with the news that their data has been encrypted. They are instructed to email the email address provided and to insert their unique ID into the title of the email so that they can be identified by the threat actor.
Free Decryption as Guarantee:
In the next section, the victim is notified that they will be afforded the ability to decrypt a sample file as proof that the threat actor is capable of decrypting files, This is meant to give the victim comfort that if they pay, they will get a working decryption tool
How to Obtain Bitcoins:
In this section the victim is guided on how to procure crypto currency so that the ransom can be paid. There are certain venues that ransomware distributors try to route their victims to. These venues tend to be more lax about KYC and AML during on-boarding, which allows the victims to set up accounts faster. There are also venues that the threat actors will often specifically call out for victims to avoid. This is typically due to extended approval times for new accounts, or speed bumps to withdraw cryptocurrency after it has been purchased.
Attention!
In this section, the threat actor provides some practical advice to the victim meant to help the victim avoid common pitfalls. Interesting, all of these suggestions are accurate and should be heeded by any victim
“Do not rename encrypted files” This is practical advice. Renaming files does not remove encryption, and can impact the ability of the files to be successfully decrypted at a later time.
“Do not try to decrypt your data using third party software. It may cause permanent data loss.” This is absolutely correct. It is not possible to decrypt recent versions of Dharma with any decryption software. Use of this software can impact file structure and make decryption at a later data impossible. Do not try third party decryption software on Dharma encrypted files. It will damage the files making recovery impossible.
“Decryption of you files with the help of third parties may cause increased price (they add their price to our), or you can become the victim of a scam.” This is absolutely true. Dishonest data recovery companies prey on the emotions of ransomware victims in order to charge usurious fees. There are also lots of individual operators that stalk security forums looking for victims to DM and solicit. Beware!
DHARMA RANSOMWARE NOTE #2: SIMPLE TEXT FILE
The second most common type of Dharma Ransomware Ransom Note is a plain text file like the above. This Dharma ransom note is much more simple and just gives the victim clear directions on how to contact the threat actors.
DHARMA RANSOMWARE NOTE #3: NO RANSOM NOTE AT ALL
In a lot of Dharma Ransomware attacks, the victim does not find any note at all. This could be for a couple of reasons. Sometimes the threat actor forgets to leave one. Sometimes the note is just buried somewhere and not found. In these cases, identifying the ransomware as Dharma, and establishing the contact information of the threat actors is still possible through the file extension.
Because Dharma appends both an ID number and the threat actors email address to every encrypted file, it is possible to identify the ransomware type and threat actor through a single sample encrypted file.
What else do I need to know?
Dharma Ransomware Encrypted File Extensions
Dharma Ransomware has taken on dozens of variants over the years. Each variant appends a different unique file extension to encrypted files. While the file extension changes, the underlying encryption process, and encryption executable is fundamentally the same. A variant typically signifies that a new group has purchased a Dharma Ransomware kit, and will be uniquely identified by the file extension. This is not always the case, but there are observable differences in the communication patterns and behaviors across variants, suggesting that each variant may be its own unique group of distributors.
COMMON DHARMA RANSOMWARE FILE EXTENSIONS:
There are many different file extensions that signify Dharma Ransomware. Some of the most recent file extensions include:
.BIP .combo .gamma .arrow .betta .vanss .audit .adobe .fire .bear .back .cccmn .tron .like .gdb .myjob .risk .santa .bizer .btc .auf .heets .usa .qwx .xwx .aqva .eth .amber .stuf .ms13 .bk666 .com .qbix .bat .MERS
An encrypted file would follow the below pattern (example of a word document):
filename.doc.id-[alpha-numeric ID #].[hacker@email.com].[dharma variant file extension]
The alpha-numeric ID number is used to identify the system, sort of like an index sticky note the hacker uses to remember the machines that were encrypted.
COMMON DHARMA RANSOMWARE EMAIL ACCOUNTS
Ransomware distributors often change their email accounts for every attack, though some groups keep them consistent. The groups tend to have preferences for the email and VPN service they use. Some use common services like Gmail or AOL, while others use encrypted email services such as ProtonMail or Tutanota.
How Dharma Ransomware Is Distributed
The top attack vector for Dharma ransomware is via Remote Desktop Protocol ports or RDP. RDP a port that is commonly used for employees or services providers to access a network remotely. RDP access sidesteps endpoint protection, making lateral proliferation between endpoints, partitioned networks, and backup systems much easier to accomplish.
Attackers can breach RDP via a few different methods:
By using port scanning via websites like Shodan and then subsequently brute-forcing RDP sessions until credentials are compromised.
Purchasing and using brute-forced credentials for sale on sites like XDedic [since removed by Law Enforcement].
Phishing an employee of the company to gain access and control of their machine. Then using that access to elevate that users permission using other credential harvesting malware. This elevated access allows the attacker to move laterally around the network.
There are tens of thousands of corporate RDP credentials available for sale for as little as $3 on dark web marketplaces. The wide availability of hacked RDP credentials is a low-hanging fruit for cybercriminals looking to launch ransomware attacks.
While plenty of large organizations continue to leave this vector unsecured, smaller companies are equally complacent. Most assume they are too small to be targeted and don’t appreciate just how easily targeted they are. Many also lack the resources, people or knowledge of how to properly secure access.
How Does Dharma Ransomware Encrypt Files
Dharma encrypts files using an AES 256 algorithm. The AES key is also encrypted with an RSA 1024. This encrypted AES key is stored at the end of the encrypted file. The encryption process typically starts with mapped drives before moving onto the root of the OS drive, while also deleting the volume shadow copies.
How to Remove Dharma Ransomware Executable Files
It is strongly recommended that any machine that becomes encrypted be completely reformatted to ensure that both the ransomware executable and, more importantly, any other malware is removed in the process. The ransomware executable is typically easy for anti-virus to find and remove. Malware that assisted in the ransomware arriving on the machine and which can do longer term damage is often harder to detect. Accordingly, a full wipe and replace process should be run on any machine that becomes encrypted with Dharma Ransomware.
How to Use the Dharma Ransomware Decryptor Tool
If a victim chooses to pay the ransom amount, they are typically sent the decryption tool executable via a file sharing site. The decryptor tool follows a complex two step process that we have detailed here. If you have further questions about how decrypting Dharma Ransomware encrypted files works, please contact us.
DHARMA RANSOMWARE FREQUENTLY ASKED QUESTIONS
1. ARE THERE FREE DHARMA DECRYPTION TOOLS?
The majority of active Dharma ransomware variants can not be decrypted by any free tool or software. If you submit a file example to us, we will have a look for free and let you know. There are also good free websites that you can upload a sample file to and independently check. You should NOT pay a data recovery firm or any other service provider to research your file encryption. They will use the same free resources noted above… so don’t waste your money or time!
2. HOW DID I GET INFECTED WITH DHARMA RANSOMWARE?
Most Dharma ransomware is laid directly by a hacker that has accessed an unprotected RDP port, utilized email phishing to remote into a network via an employee’s computer, or utilized malicious attachments, downloads, application patch exploits or vulnerabilities to gain access to a network.
3. WHAT ARE RECENT DHARMA RANSOMWARE FILE EXTENSIONS?
.BIP .combo .gamma .arrow .betta .vanss .audit .adobe .fire .bear .back .cccmn .tron .like .gdb .myjob .risk .santa .bizer .btc .auf .heets .usa .qwx .xwx .aqva .eth .amber
are common file extensions. Typically an alphanumeric ID and an email address will prepend the file extension as above.
4. WHAT DOES A DHARMA RANSOM NOTICE LOOK LIKE?
Dharma ransomware hackers will leave a notice behind that will be prominent and easy to find. It commonly looks like like the image below. It includes contact information for the hacker and instructions on how to purchase cryptocurrency to pay the ransom.
Note: We do not advise that any person or company contact a hacker and negotiate directly. Cyber criminals can be difficult to communicate with. Let a professional assist you.
Example of a .Combo ransomware notice
RANSOMWARE FREQUENTLY ASKED QUESTIONS
WHAT INFORMATION DO I NEED TO PROVIDE?
You will need to provide information from both the ransom notice and a sample encrypted file. We will schedule a call to discuss the severity of the attack, the operability of your company and the likely timeline / cost of recovering from the attack. You will also need to provide identifying information on your company, and an authorized representative of your company.
HOW MUCH WILL THIS COST?
You are already being extorted; we don’t think you deserve to pay another large fee. Coveware charges flat per incident fees. Whether the case lasts one week or three weeks, our fees are flat. We do not charge spreads of fees tied to the size of the ransom amount. Our fees will never be even close to the amount of the ransom demanded by the cyber criminal, and you should be skeptical of why any other service provider would charge a fee that high.
WHAT ABOUT FIRMS THAT HAVE TOLD ME THEY CAN DECRYPT MY FILES WITHOUT PAYING THE HACKER?
You should be extremely skeptical of any data recovery firm that claims they can decrypt ransomware. Typically they are just paying the cyber criminal without your knowledge and pocketing the difference between the ransom amount and what they will charge you. Know the facts before you engage. If the ransomware IS decryptable, the tool can be found for free. If not, purchasing a key from the cyber criminal is the only way to unlock your files. While Coveware does not condone paying cyber criminals, we recognize it is often the only choice if backups are not available or have become compromised as well. If that is the case, you deserve an honest, transparent experience.
WILL THE RANSOMWARE PAYMENT BE SUCCESSFUL?
There is no guarantee that paying the ransom will result in a working decryption tool being delivered. However, Coveware believes that data aggregation can help customers make the most informed data-driven decisions. Since we handle lots of cases of the same ransomware types, we are able to share our experiences and help customers decide how to proceed.
HOW DO I UNLOCK MY FILES?
If the ransomware payment is successful, a decryption tool & key is provided by the hacker that can be used to manually decrypt your files.
HOW DO I PREVENT THIS FROM HAPPENING AGAIN?
There are some common security mis-configurations that lead to a ransomware attack. We can share some tips and resources for preventing future attacks, but encourage companies to perform a full forensic review or security assessment as soon as possible. Consistent investment in security IT is the best antidote to preventing future attacks.
WHY CHOOSE COVEWARE RANSOMWARE RECOVERY SERVICES?
FREE
RANSOMWARE ASSESSMENT
Provide a few details from the ransom notice, an example encrypted file and details of the operability of your company and budget/time. We will provide context into the severity of the attack and your options for decryption and recovery using our database of similar cases.
Identify ransomware type
Find free decryptor tools
Identify threat actor group
24x7 SUPPORT
- RANSOMWARE INCIDENT RESPONSE
We have deep experience communicating and negotiating with hackers. It’s what we do all day long! Take advantage of our experience and allow us to shoulder this burden.
Secure & safe negotiations
Proactive service
Transparent communications
Determine risks & outcomes
FILE DECRYPTION
& RECOVERY SUPPORT
Coveware has access to a ready supply of any crypto currency, and offers a 15 minute disbursement service level agreement. We also support the decryption/data recovery process.
Professional IT support
Insurance documentation
Post-incident follow up
Post-incident support
How does Coveware help our partners?
* Source: CDNet