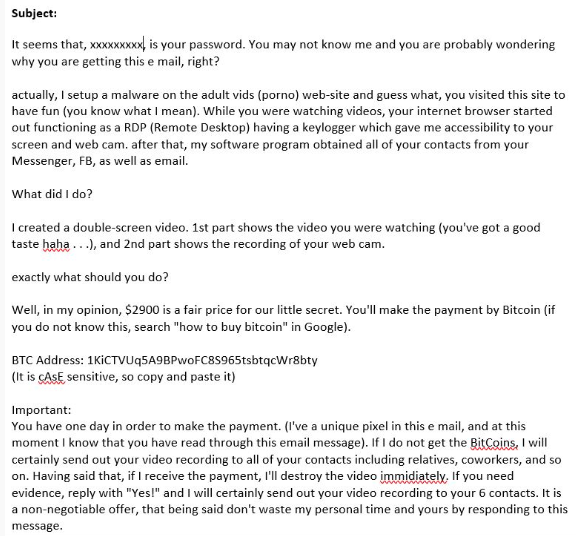
New ransomware scam preys on 'touchy' topic
Although it brings us no joy, we are writing this blog post given the prevalence of a new type of ransomware-related scam. We use the label ransomware-related, as it does not involve actual malware that encrypts files or servers. It is pure social engineering extortion. A few news articles and Bleepingcomputer had posted about it, but we are going to provide a bit more color given the cases that have arrived on our doorstep.
The headline is pretty simple: people are being extorted with the threat of releasing video of them….how shall we say this as to avoid the filters...engaging in activities consistent with viewing websites of ill repute. To date, we are confident that is 100% a scam, and that no exfiltration of images or video is actually happening (disclaimer: every case is different and nothing is a guarantee). Here is how it happens.
The criminals are using a combination of the law of averages, and some topical information to convince an individual person that they have been hacked and the sensitive images and video are in the hackers position. There are 3 elements to this:
A statistic that applies to almost everyone: In this case the hackers are leveraging the fact that human beings that are male tend to … you know. Its true for a high percentage of them.
An accelerant that legitimizes the timing: In some cases, the extortion threats are made randomly to just play the statistical odds. In other cases, there is information bespoke to the victim. We have seen cases where business travelers get the notices while staying in a hotel. We have confirmed that hotel employees have been caught scraping guest email addresses. These are presumably sold to the criminal, who then delivers the extortion threat. The likelihood of element #1 is, well higher when individuals stay in a hotels.
Specific proof of hack: As you can see in the extortion notice, the hacker sites a set of credentials in the opening line. Given that 50% of people use the same credentials across accounts, the victim is likely to assume the hack is legit given they are being shown their password. This is actually not the case. Most individuals have had their credentials spilled at some point, and they are pretty easy to find. The hacker is just searching for the email address and merging the credentials into their standard extortion threat.
This combination - knowledge of timely activity, their location, and their credentials, make the extortion threat appear legit to the victim. It is not.
Because of how ‘touchy’ this scheme is, and given that normal ransomware is often not reported to IT, we doubt most individuals will seek help for this. If you or someone you know falls victim, free services like HackNotice, which performs credentials searches can help validate that the above is true. We were able to use HackNotice to triangulate the password cited in an extortion notice to leaked credentials from a 2 year old public breach.
REGARDLESS: Shared credentials and insecure browsing are security awareness basics. Please be careful!
Image of the re-used extortion notice: