Ransomware Payments Up 33% As Maze and Sodinokibi Proliferate in Q1 2020
Ransomware Payments Increase In Evolving Distribution of Enterprise Ransomware Variants
The Coveware ransomware marketplace report aggregates observed trends from enterprise ransomware incidents in Q1 of 2020. During the first quarter of 2020 ransomware threat actors took advantage of the economic and workplace disruption caused by the COVID-19 outbreak. Spam attacks related to the outbreak surged and seldom used ‘work-from-home’ network configurations led to increased ransomware attacks across the board. Some threat actor groups continued attacking healthcare organizations, while others refused to target them. Our report shows victim demographics and resolution metrics based on actual ransomware cases handled by the Coveware Incident Response team.
The Average Ransom Payment has Increased by 33%
Average Ransom Payment
+33% from Q4 2019
In Q1 2020, the average enterprise ransom payment increased to $111,605, up 33% from Q4 of 2019. Ransomware distributors increasingly targeted large enterprises and were successful in forcing ransom payments for the safe recovery of data. Large enterprise ransom payments are the minority by volume, but the size of the payments dramatically pulled up the average ransom payment. The median ransom payment remained relatively stable at $44,021, up only slightly from the Q4 2019 median of $41,179. The stability of the median reflects the fact that most ransom payments were modest relative to the average.
Ransomware Attack Types in Q1 2020
Sodinokibi, Ryuk and Phobos remain the most common types of ransomware, Mamba follows shortly after
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q4 2019 |
|---|---|---|---|
| 1 | Sodinokibi | 26.7% | - |
| 2 | Ryuk | 19.6% | - |
| 3 | Phobos | 7.8% | - |
| 3 | Dharma | 7.8% | +1 |
| 5 | Mamba | 4.8% | +4 |
| 6 | GlobeImposter | 4.4% | +5 |
| 7 | Snatch | 2.6% | +1 |
| 8 | IEncrypt | 2.2% | +2 |
| 8 | 777 | 2.2% | +8 |
| 8 | MedusaLocker | 2.2% | +8 |
The 3 most common ransomware types remained the same between Q4 2019 and Q1 2020. Towards the end of Q1 the prevalence of Ryuk and other Hermes variants began to dissipate. The reason for this change is not currently understood.However, the change in prevalence was preceded by observable changes in threat actor behavior.
Mamba ransomware prevalence increased substantially in Q1. Mamba ransomware involves the combination of a boot-locker program and full disk encryption via commercial software. The bootloader screen is used as a ransom note. Decrypting the full disk encryption requires passwords that only the threat actor holds.
What are the Most Common Ransomware Attack Vectors?
Poorly secured Remote Desktop Protocol (RDP) access points continued to be the most common attack vector. RDP credentials to an enterprise IP address can be purchased for as little as $20 on dark marketplaces. Combined with cheap ransomware kits, the costs to carry out attacks on machines with open RDP were too economically lucrative for criminals to resist. Until the economics of carrying out ransomware balance (by either bringing the monetization success rates down or by making attacks prohibitively expensive) ransomware and cyber extortion will continue to gain prevalence.
Comparing the Top 3 Types of Ransomware - Sodinokibi, Ryuk and Phobos
In Q1 2020, the top three most prevalent types of ransomware remained the same as in Q4. Ryuk prevalence reduced dramatically as the quarter came to a close. We expect that the market share rankings will change substantially in Q2 2020, as a number of new variants have become much more active.
Comparing the Top Three Types of Ransomware by Attack Vector
The top three ransom variants employed different techniques to gain initial access to their victims. The initial access techniques tend to reflect the sophistication of the threat actor behind the attack. For example, Phobos is a very common ransomware-as-a-service variant with virtually no barriers to becoming a Phobos affiliate. Accordingly, the technical sophistication of the threat actors tends to be relatively low. These attacks typically involve purchasing previously acquired RDP credentials on a dark market.
On the other end of the spectrum, Ryuk ransomware typically relies on integrations with sophisticated spear phishing and banking trojan integrations, such as Trickbot / Emotet, that enter organizations via a subtle and strategic attack vector. Sodinokibi combined both a RaaS distribution model and sophisticated initial breach techniques. Sodinokibi used several regular strategies to gain access to their targets of choice which tend to be IT managed service providers.
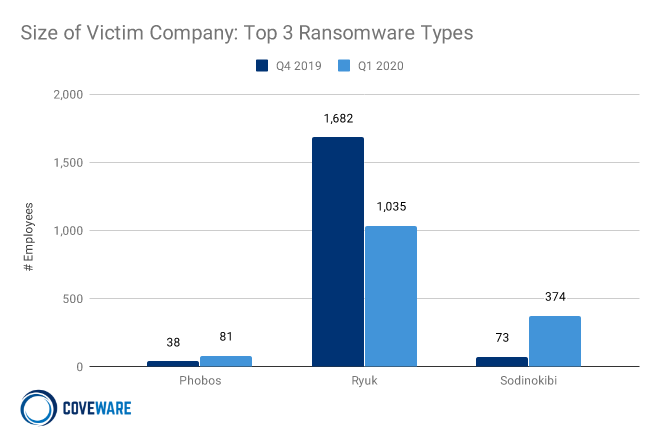
Comparing the Top Three Types of Ransomware by the Size of the Victim Company
Another distinguishing element of the three most prevalent ransomware types was the size of the target organization. In Q1, Phobos went slightly up market and successfully attacked a few larger enterprises, even though the median size of a Phobos victim remained small. The Ryuk groups shifted their focus slightly down market as the average size of their victims fell by nearly a third. Sodinokibi shifted some of their attention from small MSPs to attack select large enterprises. The change reflects their ability to employ a variety of exploits. In Q1 2020 Coveware observed Sodinokibi take advantage of several VPN vulnerabilities that were common among large enterprises.
Comparing the Top Three Types of Ransomware by Ransom Payment
Payment amounts between ransomware variants also reflect how attack patterns and targets changed. Phobos stayed relatively consistent, as the variant typically only targeted small companies that had open RDP. Ryuk amounts increased, despite a decrease in the size of targeted companies. The Ryuk amounts increased shortly after the new year, with both higher initial and final demands from their victims.
Sodinokibi ransom payments were more broadly distributed, representative of their broader victim demographic. A single large organization may have a million dollar ransom demand. Other times Sodinokibi targeted an MSP’s clients and tried to extort each individual end client for $5-$10k.
Companies Targeted by Ransomware
Public Sector Organizations Jumped in Prevalence
Small and medium sized professional service firms such as law firms, IT managed service providers and CPA firms continued to be the largest industry subset targeted by ransomware in Q1 2020.
Public sector organizations also jumped in prevalence, predominantly as a result of the COVID-19 outbreak. The subset of public organizations most targeted was public schools. Typically, school systems are targeted over the summer. The timing is designed to force the company to pay before school begins. The rotation into targeting schools in March was likely precipitated by the COVID-19 pandemic which forced most school systems to rapidly offer remote learning. The hasty switch caused many schools to leave themselves vulnerable to attack, and ransomware actors took full advantage during Q1. Public sector entities were 12% of attacks in Q1 and almost 50% of those were schools with the other half a mixture of state and local organizations.
Data Recovery After Ransomware Attacks
How Much Data Was Recovered After Paying a Ransom?
When a ransomware victim is forced to pay a ransom, Coveware tracks two primary metrics to measure the outcome:
Payment Success Rate - Does the payment procure a working decryption tool? If the threat actor did not deliver the tool, then it is considered a default and will likely lead to no data being recovered.
Decryption Recovery Rate - If a decryption tool is delivered, then how effective does it decrypt the data? Files and servers can be damaged during and after both the encryption and decryption process. The performance of a decryption tool dramatically affects data recovery rates and business interruption costs.
How Often Was a Decryption Tool Delivered After Paying a Ransom?
Payment Success Rate
+1% from Q4 2019
In Q1 2020, the payment success rate rose to 99%. Coveware saw few payment defaults in Q1. That said, our rate may not reflect the average ransomware victim for two reasons. First, Coveware has been successful in counselling victims of ransomware not to engage with threat actors that have bad track records of delivering decryption tools. Our ability to forecast a default kept victims from paying a ‘dishonest’ criminal, but also increased the success rate - no payment is made, no default is possible.
Second, because Coveware only works with businesses, we do not record case outcomes for individuals. Our anecdotal review suggests that individuals have generally worse outcomes when dealing with ransomware.
PLEASE NOTE: Coveware actively tracks threat actor groups that have a high likelihood of defaulting and those that more reliable. We often advises companies NOT to pay because of the risk of payment default. Every threat actor has their own risk profile. When no payment is made, no default has the opportunity to occur. This likely makes our Payment Success Rate higher than if we were able to accurately measure success rates across every victim of ransomware. Every victim of ransomware should seek assistance navigating their incident, and not assume that this success rate will apply to their own circumstances.
Did Ransomware Decryptor's Work?
Decryption Recovery Rate
-1% from Q4 2019
In Q1 2020, the average data recovery rate slipped to 96%. The drop reflected lower data recovery rates for a few specific variants of ransomware that have a tendency to corrupt data upon encryption. Specifically, variants like Mesponinoza, DeathHiddenTear, and Buran caused data loss upon encryption and also delivered decryption tools with bugs that lead to additional data loss. The variability of average data recovery rates varied dramatically between variants. Some ransomware variants had predictable recovery rates, close to 100%, while others were as low as 40%.
Maze Ransomware Exfiltrates data - did other Ransomware Variants?
Cases with data exfiltration
Data exfiltration, where data is downloaded from victim computers and is threatened to be released publicly, became a prevalent tactic during ransomware attacks in Q1 2020. This was a big change from the previous quarter where it was virtually non-existent.
By the end of Q1 2020 the following variants regularly exfiltrated data and threatened public release as part of a ransomware attack:
Maze
Sodinokibi
DopplePaymer
Mespinoza
Netwalker
CLoP
Nephilim
In Q1, several prevalent ransomware variants combined ransomware attacks and data exfiltration threats. Maze was exfiltrating data in 99% of cases, but as they broadened their attack profile to include smaller companies the frequency of data exfiltration decreased. In Q1, Maze was the only ransomware type where the prevalence decreased.
Coveware expects data exfiltration threats to increase in 2020 as more threat actor groups try to raise conversion rates on their attacks. Some groups created public ‘news’ boards to publicly post stolen data of clients that don’t pay. Others resorted to sending the stolen data to customers, reporters or other recipients to damage the victim’s reputation.
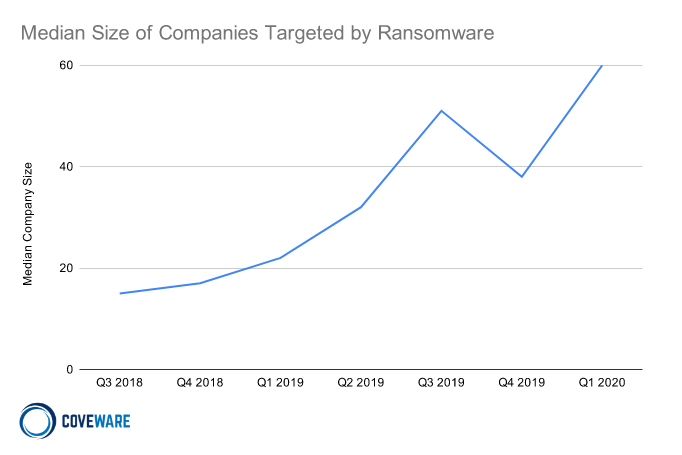
Ransomware Remains Proportionally a Problem for Small Businesses
Average # of Employees
+2.5% from Q4 2019
The shift to ‘Big Game Hunting’ stabilized as the average size organizations impacted by ransomware leveled off over the past 3 quarters. However, it is important to note that while large companies are targeted, ransomware remains proportionally a small business problem.
The median company size is still substantially lower at 62 employees, a reminder of how large enterprises can pull averages up.
Costs of Ransomware Attacks in Q1 2020
How Much Does a Ransomware Attack Cost?
The total cost of a ransomware attack is a function of the severity and duration of the attack. Financial costs include the immediate remediation of a network and its hardware. Costs also include lost revenue and potential brand damage if business interruption is severe enough. In Q1, ransomware actors combined the exfiltration of data from victims into their attacks. This data exfiltration is intended to force victims of ransomware into paying, even if they were able to recover lost data from backups.
How Much Downtime Does a Ransomware Attack Cause?
Average Days of Downtime
-7% from Q4 2019
Average days of downtime leveled off in Q1 2020 at 15 days per ransomware attack, down slightly from Q4 2019. Even though the average stabilized, 2 weeks of impaired productivity is a substantial amount of time for any business. Business interruption costs from downtime are the largest pain point for companies impacted by a ransomware attack. An organization’s ability to persevere through extended disruption depends on their size and industry.
Hospitals are most acutely at risk of downtime due to the potential impact on patient care. It is worth noting that some threat actors made public announcements that they would not target healthcare organizations. Other ransomware variants continued to target hospitals, including Ryuk, DopplePaymer and Defray777.
What Cryptocurrencies Are Used to Pay for Ransomware?
Payments using Bitcoin
Flat from Q4 2019
Bitcoin continued to be the cryptocurrency of choice for cyber extortion. This was principally due to the relative ease with which Bitcoin can be procured when compared to more esoteric types of cryptocurrency. In our analysis of Bitcoin payments, it is clear that Bitcoin is typically swapped into privacy coins like Monero or Dash to reduce traceability of the funds before the cryptocurrencies are washed back through to fiat currency. Some threat actor groups are now making their initial demands in Monero to reduce traceability earlier in the laundering cycle.
Disclaimer
Coveware is not responsible for any actions taken, errors or omissions (negligent or otherwise), regardless of the cause, or for the results obtained from the use of this content, or for the performance of any computer, hardware or software used or modified in conjunction with this content. The content is provided on an "as is" basis.
VIEWERS OF THIS REPORT AND ITS CONTENT DISCLAIM ANY AND ALL EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE OR USE, FREEDOM FROM BUGS, SOFTWARE ERRORS OR DEFECTS, THAT THE CONTENT'S FUNCTIONING WILL BE UNINTERRUPTED OR THAT THE CONTENT WILL OPERATE WITH ANY SOFTWARE OR HARDWARE CONFIGURATION.
In no event shall Coveware be liable to any party for any direct, indirect, incidental, exemplary, compensatory, punitive, special or consequential damages, costs, expenses, legal fees, or losses (including, without limitation, lost income or lost profits and opportunity costs or losses caused by negligence) in connection with any use of the content even if advised of the possibility of such damages.