Ransomware attack on MSPs exploits popular PSA/RMM Tool
A ‘cleanup set’ in surfing parlance refers to a large set of waves that break before the line up of waiting surfers. When a surfer yells “Outside!” it is an urgent warning to start paddling for deeper water, and avoid being cleaned out.
The managed service provider (MSP) equivalent of a cleanup set recently occurred, and a member of the security community had been yelling ‘Outside!’ for two years.
Clean up set wipes out the line up
PSA/RMM Exploit on Popular MSP Tool Disclosed Two Years Ago
Two years ago, in November of 2017, security researcher Alex Wilson published research on a vulnerability in the ConnectWise ManagedITSync integration; a utility designed to sync data between the ConnectWise Manage PSA and the Kaseya VSA RMM. These tools are popular among MSPs, the primary provider of IT support for businesses under 100 employees.
The vulnerability that Alex found allowed a remote attacker to execute SQL commands on the Kaseya VSA database. In turn, the attacker could create administrative users, change user passwords, and create tasks to automatically deploy malicious software, like ransomware to all endpoints under an MSP’s management. The vulnerability was tagged CVE-2017-18362 and remains under analysis as of February 5th 2019.
Alex’s ‘Outside!’ warning was not acknowledged until the cleanup set came through. In this analogy, the devastation took the form of GandCrab 5.1 ransomware, which was detonated on the end points of vulnerable MSP end clients.
Ransomware Cripples a Single MSP’s Entire Clientele Base
Last week, the vulnerability CVE-2017-18362 got the sort of attention nobody wanted. A Reddit post detailed at least one MSP who had not patched this vulnerability and was hit with a debilitating blow.
By exploiting the vulnerability, attackers gained administrative access to the MSP’s client management tools and installed GandCrab ransomware to every endpoint under the MSP’s control. Nearly every client of the MSP had their machines encrypted. Based on the MSP cases handled by Coveware (note, Coveware was not involved in the case detailed on Reddit), we believe the attacks may have further leveraged new automated credential stealing kits to further the attacks. Huntress Labs has detailed some aspects of the vulnerability as well.
How Ransomware Attacks on MSPs Exponentially Increase the Impact
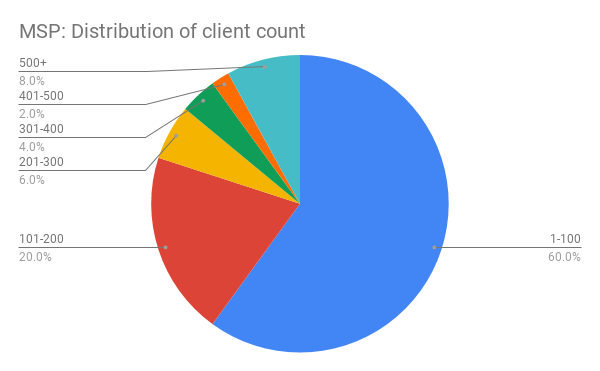
Managed Service Providers are outsourced IT experts and are the main source of IT support to the small businesses globally. According to a recent report by Datto, 80% of MSPs have less than 200 end clients and these clients tend to be small businesses with only a few employees.
MSP utilities like RMM or PSA allow them to scale monitoring and troubleshooting of their client’s networks. They can remotely troubleshoot issues, push updates and patches, and address alerts quickly. These are fundamental tasks to scaling a MSP, and without them most small businesses would not be able to afford any IT support.
Distribution of how many end clients most MSPs have
However, in the same manner that RMM and PSA tools have made productive mass management possible, vulnerabilities in these tools can expose the end businesses to simultaneous and mass attack.
Similar Attack Pattern, New Attack Vector
The attack patterns observed were similar to attacks we see leveraged directly against businesses. In essence, the vulnerability was used to gain elevated credentials whereby AV & endpoint protection was disabled, and primary servers and backups were encrypted.
The MSP-based attack was amplified as the attack pattern was scripted via the RMM/PSA software and pushed to each underlying business. The automation of the attack dramatically magnified its scale and impact. It is estimated that 1,500 to 2,000 systems belonging to the MSP's were impacted, with the aggregate ransom for the Reddit case reportedly reaching over $2.6 million.
Given the tight communication circles that MSPs frequent, we hope that all MSPs have heeded this cautionary tale and patched any vulnerable PSA/ RMM integrations. We also note that best practices including ‘least privileges’ and 2FA on administrative accounts can help prevent ransomware attacks like these.
Current or prospective MSPs partners of Coveware are welcome to contact us to discuss in greater depth.