RaaS devs hurt their credibility by cheating affiliates in Q1 2024
Following the FBI disruption of BlackCat ALPHV in Q4, a global Law Enforcement Agency (LEA) consortium also successfully disrupted the LockBit Ransomware-as-a-Service (RaaS) organization which included sanctions on two members of the LockBit organization. While neither of these operations have completely shuttered BlackCat or LockBit, the show of force by LEAs was effective in shaking the confidence of ransomware affiliates and RaaS developers. The actions demonstrated that threat actor infrastructure and potentially identifying information on its owners and affiliates is well within the potential reach of Western law enforcement organizations.
The response to these disruptions by the RaaS developers was perplexing. Rather than take steps to shore up affiliate confidence in their operations and operating model, several RaaS brands did the exact opposite by engaging in highly public negative behavior that likely exacerbated the migration of ransomware affiliates away from their brands. First, the LockBit group allowed a dispute about a payment split between operator and affiliate to spill onto the forums. The details of the dispute demonstrated that the group had no issue cutting an affiliate out from their share of a payment. While the actual truth will never be known, it is perplexing that such a large and profitable group would allow such a dispute to go unresolved given that the amount of the dispute (estimated in the low seven figures) likely paled in comparison to the publicity damage that it caused.
Later in the month, BlackCat disappeared in a likely exit scam which potentially left their affiliates high and dry. This action was equally perplexing given that there is ample precedent for RaaS groups shutting down gracefully and attempting to preserve their reputations and future opportunities to reemerge. Both the LockBit and BlackCat actions have caused a mass diaspora of ransomware affiliates that are deciding where to go and what to do with themselves. The likely next steps for what could be hundreds of ransomware affiliates can be bucketed into the following categories:
Give Up on Cyber Crime. There is no doubt that one of the healthy by-products of LEA takedowns and RaaS/Affiliate swindles has caused some individual affiliates to hang up their cyber crime spurs. Most participants in the cyber extortion ecosystems are not hardened criminals, rather they are individuals with STEM skills that live in jurisdictions lacking both extradition treaties, and sufficient legitimate economic opportunities to put their skills to use. Some of these people will view the increased risk of getting in trouble along with the risk of getting cut out of their income as enough reason to quit.
Give Up on Working Inside of RaaS Brands. Much like option 1, many affiliates will think through the risk/return profile of re-aligning with a new RaaS organization and opt to stay in the cyber extortion ecosystem, BUT roll their own infrastructure to control their own narrative. Since many highly functional ransomware builders have been leaked, including Conti’s and Babuk, we expect a growing number of ransomware affiliates to leverage these free resources and develop their own encryption operations. We have already seen an increase in Babuk forks in recent attacks, and several former RaaS affiliates using the ubiquitous, and almost free, Dharma / Phobos services.
Remain with RaaS and Roll the Dice. We are not predicting the death of the RaaS model, but the events of Q1 are not an anomaly. They are actually a continuation of a long term trend, with ransomware developers having a quiet history of swindling their own affiliates, highlighted by the steps REvil took to cheat their affiliates back in 2021. Ransomware affiliates that don’t study history will be doomed to play a role in its repetition.
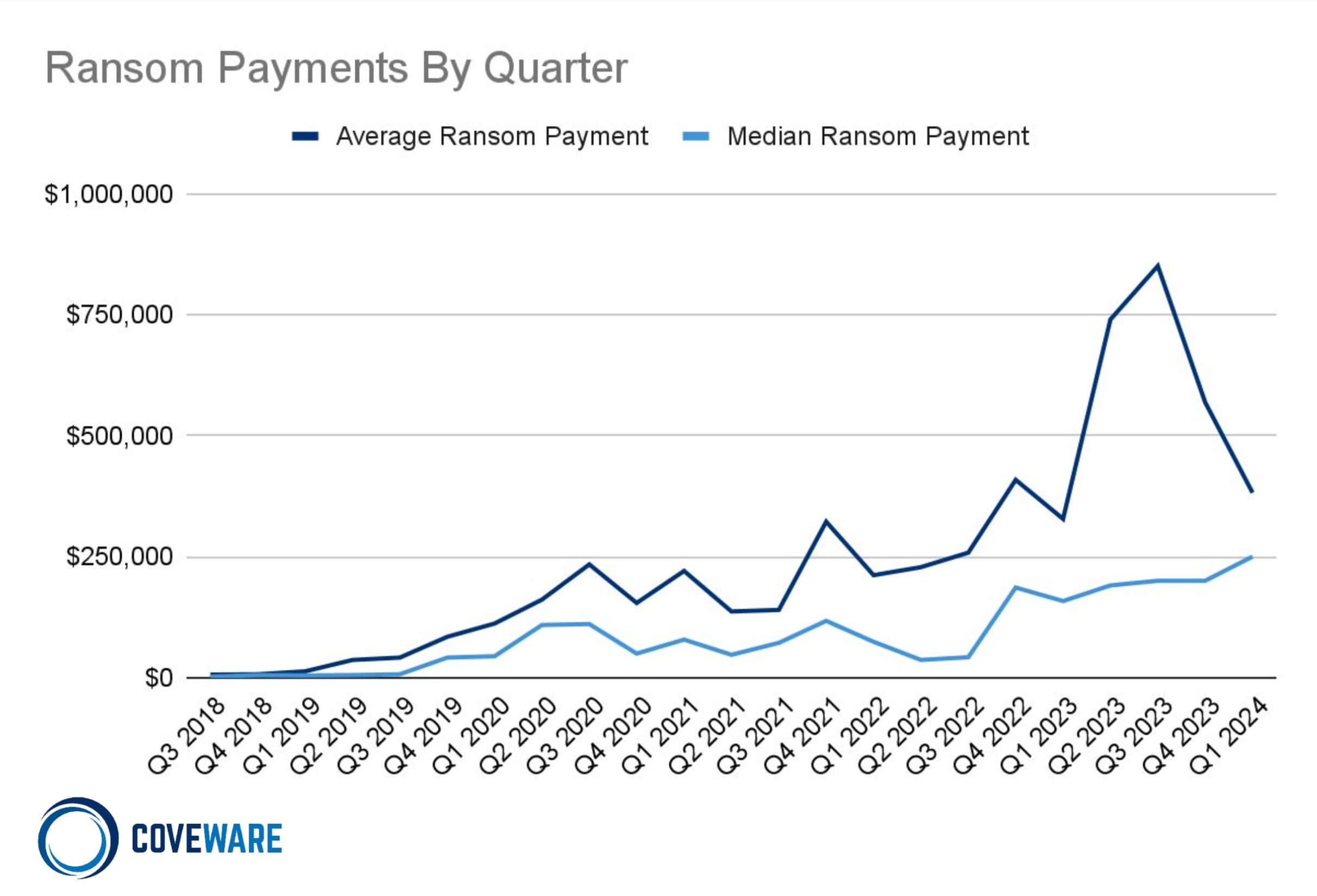
Ransom Payment Amounts by Average and Median in Q1 2024
Average Ransom Payment
-32% from Q4 2023
Median Ransom Payment
+25% from Q4 2023
In Q1 of this year, the average ransom payment continued its downward trend, decreasing 32% from Q4 2023 to $381,980. The median ransom payment lifted by 25% to $250,000. As less companies succumb to paying ransoms, there is a compounding effect on the amount of average payment. It is evident that rather than shoot for the moon with a very high initial demand, many ransomware affiliates are opting for the opposite tactic, and are demanding more reasonable amounts. The intention of this tactic is to keep more victims engaged and at the negotiating table with a reasonable demand versus scaring victims away from even engaging with a fantastical initial demand.
Ransom Payment Rates in Q1 2024
In Q1 2024, the proportion of victims that chose to pay touched a new record low of 28%. While Coveware does not have eyes on every cyber extortion event, we do see a large enough cross section of incidents to draw inferences. Enterprises large and small are increasingly able to withstand an encryption attack, and restore their operations without the need for a threat actor decryption key. Additionally, we saw a continuation of long-tailed data exfiltration defaults by threat actors in Q1, i.e., posting of information on a leak site after payment or “hostage trading” with other groups or individuals, which adds further evidence to the file on the lack of benefits to pay for suppressing a data leak or any confidence in a criminal actor keeping their word.
During Q1, 23% of victims opted to pay when their incident ONLY involved the publication of stolen data (i.e., the victim was not faced with needing a decryption key as part of their decision making process). Bolstering the decision against payment has been the resurfacing of previously stolen data, that victims HAD previously paid to suppress. LockBit was found to still be holding the stolen data of victims that had paid a ransom, and we have also seen prior Hive victims that had paid the extortion, have their data posted on the Hunters International leak site (a reboot / rebrand of Hive). Much like the lessons being learned by ransomware affiliates, future victims of data exfiltration extortion are getting more evidence daily that payments to suppress leaks have little efficacy in the short and long term.
Most Common Ransomware Variants in Q1 2024
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q4 2023 |
|---|---|---|---|
| 1 | Akira | 21% | - |
| 2 | Black Basta | 9% | New in Top Variants |
| 2 | Lockbit 3.0 | 9% | +1 |
| 3 | Medusa | 6% | +2 |
| 3 | Phobos | 6% | +4 |
| 3 | BlackCat | 6% | -1 |
| 4 | Rhysida | 4% | New in Top Variants |
| 4 | BlackSuit | 4% | New in Top Variants |
| 4 | Inc Ransom | 4% | New in Top Variants |
Market Share of the Ransomware attacks
For the third straight quarter, Akira held its position at the top of our rankings. The LEA actions and credibility issues of both LockBit and BlackCat pushed alternative variants into the top rankings, including the continued resurgence in Black Basta, a trend we expect to follow through into Q2. It is clear that ransom affiliates that ARE choosing to stay in the RaaS model are choosing either Akira, Black Basta or BlackSuit, while the lift in Phobos signals that some affiliates are already choosing to roll their own operations.
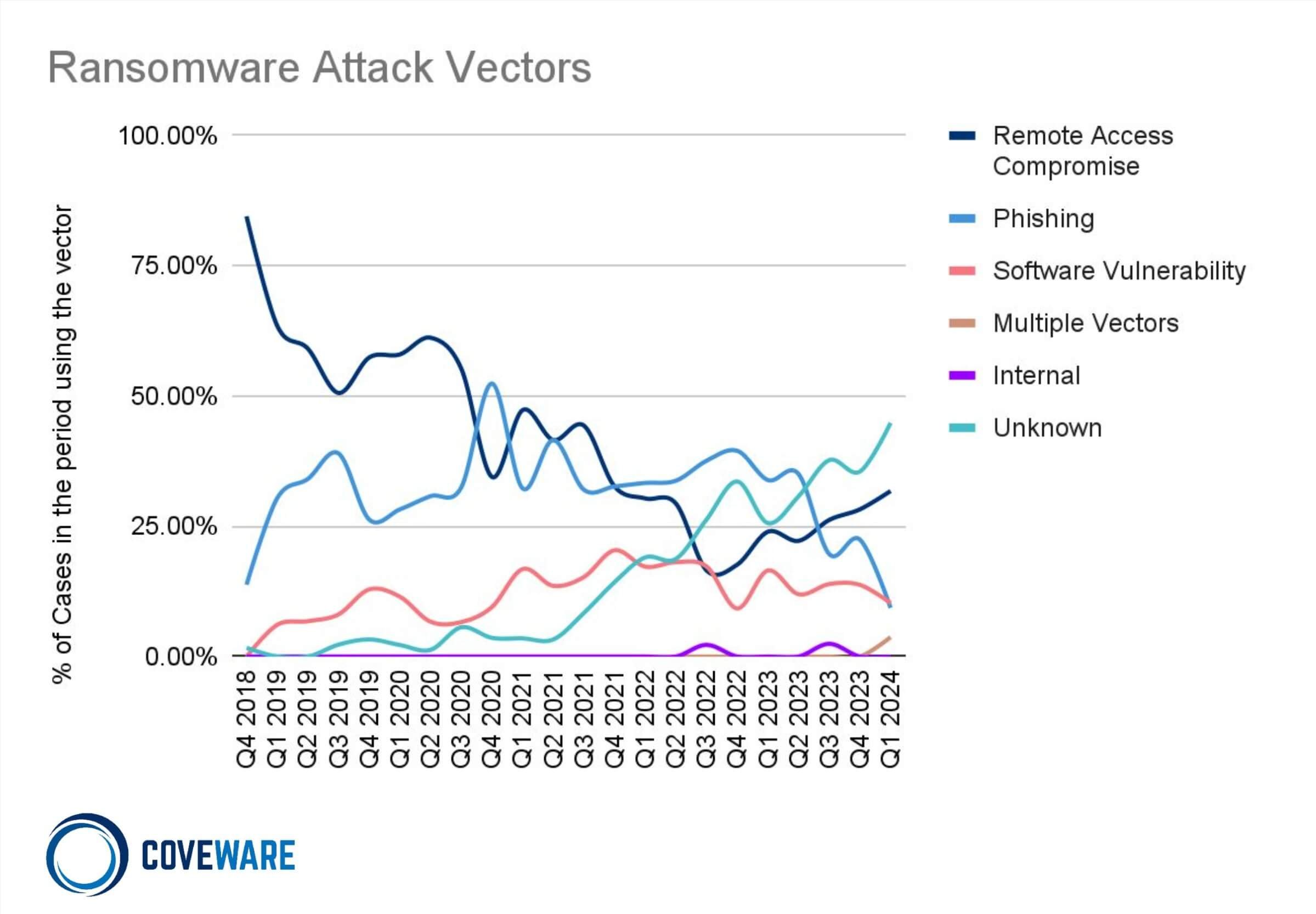
Attack Vectors in Q1 2024
In Q1, anti-forensic tactics led to a rise in attacks where the original attack vector remained unknown. It should be noted that while the clear attack vector may be unidentified by forensics, the initial access is typically just one of a dozen or so tactics necessary to achieve extortion level impact, often chained together (e.g., email phishing, RDP compromise, software vulnerability). Too often we see victims solely focused on ‘patient zero’ and the initial vector, leading to an overpivot in prevention and detection tooling and techniques against that vector. Unlike a pandemic disease, an enterprise's comorbidities (other security weaknesses / vulnerabilities) are far more important and addressable than just the initial vector, and like a strong immune system require multiple layers of defenses to maintain health and wellness. Threat actors continued to harvest from the land of plenty in critical vulnerabilities (CVEs) that were left unpatched or unmitigated, most notably:
CVE-2023-20269 initially published in September 2023, which was principally leveraged by Akira to access two different Cisco VPN products
CVE-2023-4966 initially published in October 2023, which was leveraged by RansomHouse, BlackSuit, Play and Lockbit to impact Netscaler VPN virtual servers
CVE-2024-1708-9, published in February 2024, which is used by Mamba and RansomHouse for remote code execution against certain versions of unpatched ScreenConnect instances.
With the exception of the ScreenConnect vulnerability, the majority of observed exploitation was weeks or months after the release of the critical CVE. While zero day vulnerabilities remain potentially highly impactful and exploitable, the majority of threat actors are more often able to leverage previously known vulnerabilities with documented exploit paths, in conjunction with an organization’s lagging or weak vulnerability management program, for initial access.
Exfiltration [TA0010]: Exfiltration returned to the top of our observed tactics in Q1. Exfiltration consists of techniques that threat actors may use to steal data from a network. Once data is internally staged, threat actors often package it using a combination of compression and encryption software to avoid detection while exfiltrating it from the bounds of a network. Techniques for getting data out of a target network typically include transferring stolen data over threat actor command and control channels, but most commonly use file transfer and synchronization tools combined with exploiting outbound server access (e.g., 443/HTTPS) to the Internet. Common third party exfiltration tools used in these instances include Megasync, Rclone, Filezilla, and Windows Secure Copy (WinSCP). Some actors have clear tool favorites. For instance, Akira prefers WinSCP while BlackCat and the Scattered Spider groups prefer Filezilla. These preferences though do not preclude a threat actor for using other solutions in their toolbox.
Impact [TA0040]: Unsurprising as it relates to ransomware, impact to data maintains a top spot in our tactics in Q1. Impact consists of techniques used by adversaries to disrupt the availability or compromise the integrity of the business and operational processes. Techniques used for impact can include destroying or tampering with data along with encryption. In some cases, business processes can look fine, but may have been altered to benefit the adversaries’ goals. These techniques might be used by adversaries to follow through on their end goal or to provide cover for a confidentiality breach, as well as inhibit system recovery by deleting information such as Windows Volume Shadow Copies. Ransomware itself has long shed any notion of a Windows specific problem, with ransomware binaries compiled for Windows, Linux, as well as VMWare ESXi. ESXi has been a favored target of many groups due to the “jackpot” nature of disrupting a virtualized host or cluster of hosts, impacting multiple applications and databases, as well as security challenges with proper configuration and hardening, and lack of security tools capable of running on ESXi. This may also include tampering with credentials to deny access to the ESXi virtual environments. This is a very common tactic used by ransomware groups such as Akira, NoEscape, and Rhysida.
Lateral Movement [TA0008]: Lateral Movement by threat actors consists of techniques used to enter and control remote systems on a network. Successful ransomware attacks require exploring the network to find key assets such as domain controllers, file share servers, databases, and continuity assets that are not properly segmented. Reaching these assets often involves pivoting through multiple systems and accounts to gain access. Adversaries might install their own remote access tools to accomplish Lateral Movement but often use legitimate credentials or those created by the threat actor along with native network and operating system tools, which may be stealthier and harder to track. The usage of internal Remote Desktop Protocol (RDP) remains one of the fastest and most efficient methods for lateral movement if a threat actor has the proper credentials. Other favored tactics involve the exploitation of SMB/Windows Admin Shares, remote controls tools like VNC, and using SSH (e.g., Putty) for lateral movement.
Discovery [TA0007]: Threat actors often use Discovery techniques to gain knowledge about a target’s internal network. These techniques help adversaries observe the environment and orient themselves before deciding how to navigate the network to achieve their impact objectives. This may occur on the initial workstations compromised at the onset of the attack, as well as from privileged systems such as domain controllers when staging the ransomware and targets for the encryption. Native operating system tools are often used toward this post-compromise information-gathering objective.
Command and Control [TA0011]: Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Threat Actors commonly attempt to mimic normal, expected traffic to avoid detection. While instances of what would be considered “traditional” C2 tooling are still observed (e.g., Cobalt Strike, Impacket, Metasploit), TA preferences continue towards the use of legitimate remote management and monitoring (RMM) software, leveraging trusted domains and signed executables, to maintain an interactive session on victim systems. These tools may already be installed in the environment and conscripted by the threat actor, but often are downloaded into the environment after initial access has been achieved. Common tools in use include AnyDesk, ScreenConnect, TeamViewer, LogMeIn and TightVNC. Some of these tools have unique feature functions attractive to a TA, such as ScreenConnect’s ‘backstage mode’ feature, which allows for complete access to the Windows terminal and PowerShell without the logged-on user being aware which makes it a particularly effective tool. The list of exploited and conscripted tools grows each quarter, with recent additions such as RustDesk being used by groups like Akira, NoEscape, and DragonForce.
When compared to post-exploitation channels that heavily rely on terminals, such as Cobalt Strike or Metasploit, the graphical user interface provided by RMMs are more user friendly. With the popularity of SaaS (Software as a Service) models, many RMMs are further offered as cloud-based services requiring only an outbound HTTPS/443 connection to the Internet to operate. By having command & control channels rely on legitimate cloud services, adversaries make attribution and disruption more complex.
Ransomware Victimology Demographics
Impacted Industries
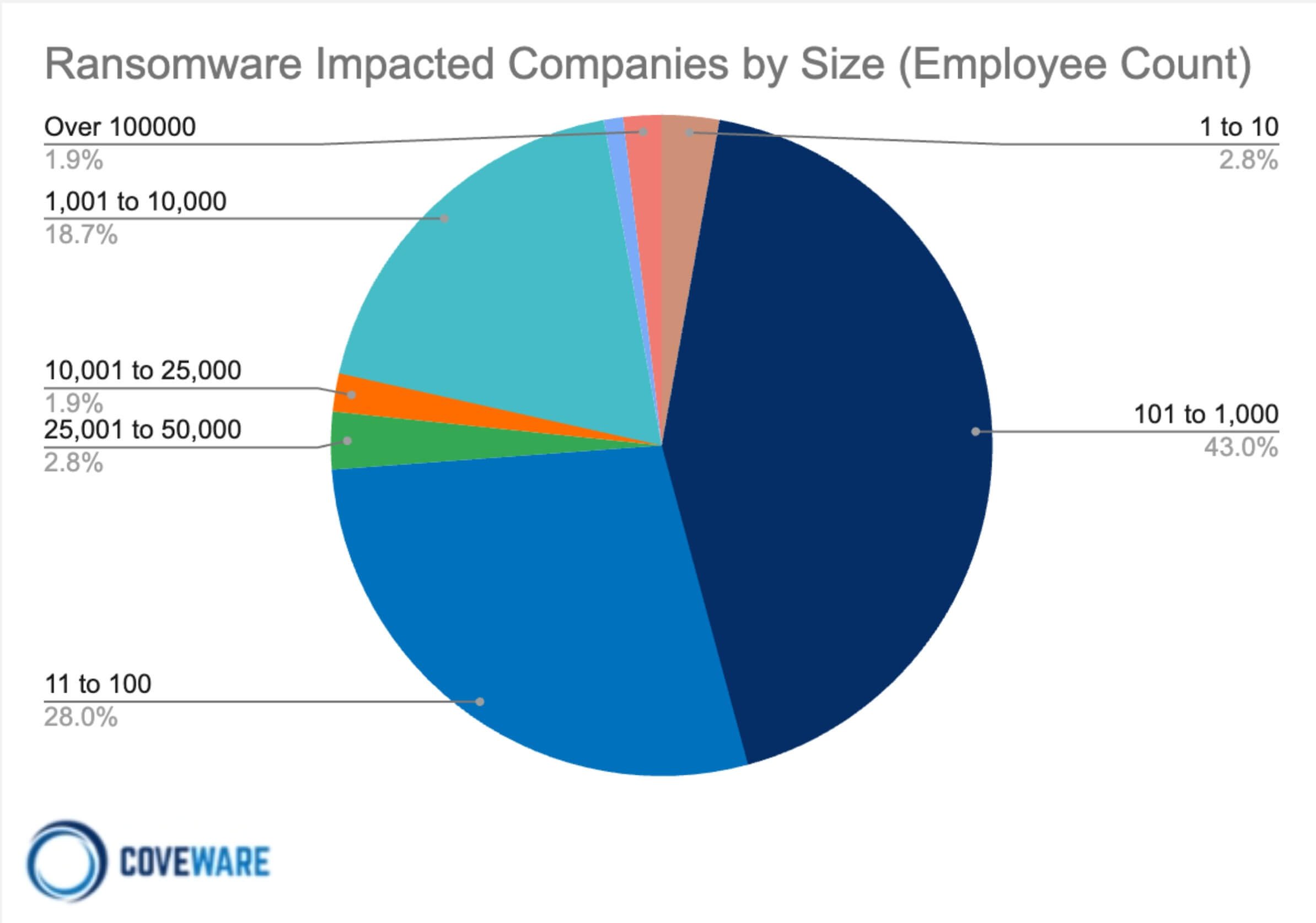
Impacted Companies by Size
Threat actors continue to live off the land in Q1 of 2024. Ransomware remains predominantly a crime of opportunity, not a targeted activity, though there is some data to suggest certain groups like BlackCat made a concerted effort NOT to exempt Healthcare from their victim portfolios as they may have tried to do in prior quarters. As the ransomware affiliate diaspora spreads further in 2024, we expect threat actors to continue to leverage any vulnerabilities available to them with little regard for who the victim enterprise is, or what industry the victim is in. This is especially true in a landscape where “easy” victims are hard to come by and threat actors will be forced to adopt a “take what we can get” approach.