Improved Security and Backups Result in Record Low Number of Ransomware Payments
FEWER Ransomware Victims Are Paying
Over the last 4 years, the propensity for victims of ransomware to pay a ransom has fallen dramatically, from 85% of victims in Q1 of 2019, to 37% of victims in Q4 of 2022. On an annual basis, 41% of victims paid in 2022 vs. 76% in 2019. Despite the best efforts of the cyber criminals rowing in the opposite direction, shaving 48 whole percentage points of this key indicator has been the result of several factors.
Key Factor #1: Enterprises are investing substantially more in security and incident response planning. A heightened appreciation for existential risk of a ransomware attack has substantially increased funding to enterprise security and incident response teams. High-profile attacks such as Colonial Pipeline were very effective in kicking off a fresh wave of investment in security and continuity assets. This is clearly personified in a major bump in keyword search volume and frequency for such terms as “Immutable Backups.”
Companies that are better able to defend themselves do not succumb to attacks as frequently. Enterprises with well-practiced incident response processes are less likely to experience material impact (which may result in a ransom payment) when an attack is successful. Less successful attacks and fewer attacks that necessitate a payment have squeezed the overall probability of payment down and to the right.
Key Factor #2: Law enforcement agencies such as the FBI have subtly but effectively shifted strategy from pursuing just arrests to putting a focus on helping victims, and imposing costs to the economic levers that make cyber-crime so profitable. We at Coveware have seen the tangible results this strategic shift has had on the outcome of scores of ransomware victims. We hope the agency continues to lean into this strategy in 2023 and beyond as it is clearly working.
Factor #3: When unit economics of a profitable industry shrink, the contraction tends to compound on itself, causing exponential decline versus linear decline. As the absolute dollar amount of ransom proceeds produced by the cyber extortion economy shrinks, the operating costs to carry out an attack increase. As less victims pay, the profitability to the criminals shrinks, and the cycle repeats in a compounding manner. The end result is a smaller number of cyber criminals actors that can make a living distributing ransomware, and ultimately fewer attacks. As we have long discussed, attacking the economics of cyber-crime is the most effective way to counter the threat of ransomware.
Average and median ransom Payment in Q4 2022
Average Ransom Payment
+58% from Q3 2022
Median Ransom Payment
+342% from Q3 2022
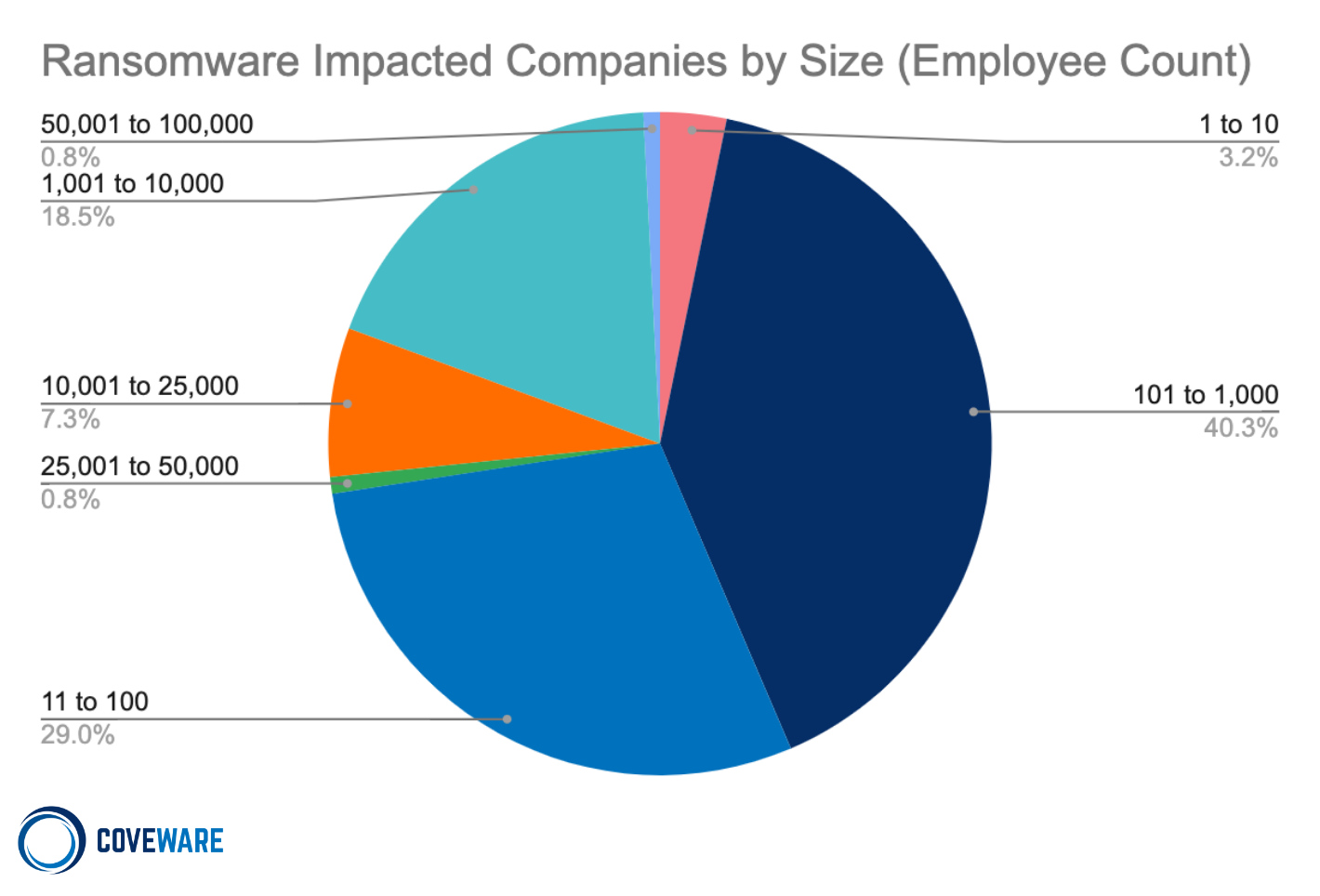
Why are the average ($408,643 +58% from Q3 2022) and median ($185,972 +342% from Q3 2022) increasing if fewer companies are actually paying? As the expected profitability of a given ransomware attack declines for cyber-criminals, they have attempted to compensate by adjusting their own tactics. First, the median victim size increased during the quarter (275 employees, +10% from Q3 2022). Threat actors are moving slightly up the market to try and justify larger initial demands in the hopes that they result in large ransom payments, even as their own success rate declines.
Another sign that the absolute value of ransom payments is declining and affecting threat actor behavior are incidents that involve the threat actor making a second demand for more money after an initial ransom is paid (we refer to this as re-extortion. Note this is NOT the same as ‘double extortion,’ which is when the threat actor encrypts a network and exfiltrates data). Re-extortion has historically been a tactic used principally by lower-end ransomware groups that attack smaller companies. In 2021, the top 10 most likely ransomware variants to re-extort victims were:
Makop
Dharma
Phobos
Waiting
Lone Wolf Actors
Avaddon
CryLocker
Haron
Hello Kitty
Lockbit
Note that Makop, Dharma, Phobos, and Waiting are all very similar ransomware as a service variants that are open to any threat actor. Victims are typically very small businesses. In 2022, the same list grew to include some well known closed Ransomware-as-a-service (RaaS) variants that typically target mid-market and larger enterprises:
Phobos
Dharma
Quantum
Artemis
BlackByte
Vice Society
Conti
Hive
Lone Wolf Actors
Snatch
The increased prevalence of the re-extortion tactic in RaaS variants that target larger companies is an indicator of financial strain. Threat actors are becoming less willing to let go of a paying victim without trying to extract as much as possible. The willingness of self-described “reputable” threat groups to engage in this amateur deception tactic exemplifies the “wild west” nature of the current extortion landscape. RaaS groups care less than their predecessors about upholding their reputation, and the absence of deceptive behavior in previous negotiations should not be viewed as a reliable forecaster that they will abstain from deception in the future. Ransomware actors are first and foremost driven by economics, and when the economics are dire enough, they will stoop to levels of deception and duplicity to recoup their losses.
Most Commonly Observed Ransomware Variants in Q4 2022
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q3 2022 |
|---|---|---|---|
| 1 | Hive | 13.8% | +1 |
| 2 | Black Basta | 12.2% | +1 |
| 3 | BlackCat | 10.6% | -2 |
| 4 | Royal | 8.9% | New in Top Variants |
| 5 | Phobos | 6.5% | -1 |
| 6 | Quantum | 4.8% | New in Top Variants |
| 7 | Diavol | 3.2% | New in Top Variants |
| 7 | Lockbit 3.0 | 3.2% | New in Top Variants |
Market Share of the Ransomware attacks
While RaaS brands continue to absorb the bulk of the market share of attacks, the ability for RaaS affiliates to move between RaaS brands has become completely fluid. There is no brand loyalty by affiliates as there was in 2019 and 2020. We have observed so many crossovers by affiliates between the major brands, that it is no longer noteworthy or indicative of anything. A given cybercriminal can pick and choose which RaaS brand they want to use on a given attack with the same ease that they select which color of tee shirt to wear on a given day.
Ransomware Attack Vectors and MITRE ATT&CK TTPs Observed in Q4 2022
Common TTPs used in attacks do not change radically quarter to quarter. Threat actors will always gravitate towards TTPs that maximize profits. TTPs that produce profits are repeated until the margins disappear. Below are most common TTPs observed in attacks, mapped to the MITRE ATT&CK framework.
Impact: [TA0040] Impact consists of techniques used by adversaries to disrupt the availability or compromise the integrity of the business and operational processes. Techniques used for impact can include destroying or tampering with data. In some cases, business processes can look fine, but may have been altered to benefit the adversaries’ goals. These techniques might be used by adversaries to follow through on their end goal or to provide cover for a confidentiality breach.
Data Encrypted for Impact [T1486]: Encryption of files is the most common form of impact observed. This may include forensics logs and artifacts as well that may inhibit an investigation.
Service Stop [T1489]: Threat actors often disable services related to detection, or backup replication to maximize the impact of encryption.
Data Destruction [T1485]: Most of the time, data destruction is aimed at the destruction of forensic artifacts via the use of SDelete or CCleaner. Unfortunately, sometimes ransomware actors destroy production data stores (sometimes malicious, sometimes by accident).
Resource Hijacking [T1496]: It is very common to find cryptocurrency mining software in the environments of impacted enterprises.
Lateral Movement [TA0008]: Lateral Movement by threat actors consists of techniques used to enter and control remote systems on a network. Successful ransomware attacks require exploring the network to find key assets such as domain controllers, file share servers, databases, and continuity assets that are not properly segmented. Reaching these assets often involves pivoting through multiple systems and accounts to gain access. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier and harder to track. The two most observed forms of lateral movement are:
Remote Services [T1021], which is primarily the use of VNC (like TightVNC) to allow remote access or SMB/Windows Admin Shares. Admin Shares are an easy way to share/access tools and malware. These are hidden from users and are only accessible to Administrators. Threat actors using Cobalt Strike almost always place it in an Admin share.
Lateral Tool transfer [T1570]:Primarily correlates to the use of PSexec, which is a legitimate windows administrative tool. Threat actors leverage this tool to move laterally or to mass deploy malware across multiple machines.
Discovery [TA0007]: Threat actors use Discovery techniques to gain knowledge about a target’s internal network. These techniques help adversaries observe the environment and orient themselves before deciding how to navigate the network to achieve their impact objectives. Native operating system tools are often used toward this post-compromise information-gathering objective. The most observed tactics of discovery we observed in Q4 were:
Network Service Scanning (T1046): Primarily consists of abusing Advanced IP Scanners to identify what network hosts are available.
Process Discovery (T1057): Tools commonly abused are Process Explorer or Process Hacker, which allow threat actors to check active processes and kill them.
System Owner/User Discovery (T1033): A tactic used to get a listing of accounts on a system or network such as the use of ‘whoami’ command to identify the username from a system.
Domain Trust Discovery [T1482]: Can involve the use of custom scripts or tools like AdFind to gather information on domain trust relationships and identify ways for a threat actor to move lateral movement
System Networks Connections Discovery [T1049]: A common tool used for this network enumeration tactic is Bloodhound.
System Information Discovery [T1082]: Typically involves the use of PSinfo, which reports back a variety of information like the kernel build, the owner, and processor capacity.
Account Discovery [T1087]: Used by a small subset of cases where the threat actor uses Sharphound to collect domain information.
Command and Control [TA0011]: Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. There are many ways an adversary can establish command and control with various levels of stealth depending on the victim’s network structure and defenses:
Remote Access Software [T1219]: Ransomware threat actors will use legitimate software to maintain an interactive session on victim systems. Common tools observed in Q3 were AnyDesk, TeamViewer, LogMeIn and TightVNC.
Ingress Tool Transfer [T1105]: When establishing command and control, actors will commonly install external tools onto the controlled endpoint in order to further proliferate their movement inside a network.
Proxy: Multi-hop [T1090] tactics are used to direct network traffic to an intermediary server to avoid direct connections to threat actor command and control infrastructure.
Credential Access [TA0006]: Credential Access techniques involve theft or malicious access and control of credentials like account names and passwords. Techniques used to get credentials to include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals.
Brute Force [T1110]: Threat actors will run scripts or programs that attempt authentication access by trying millions of username and password combinations until one works. Brute forcing is primarily run against servers that have an open Remote Desktop (RDP) port (internal or external)
OS Credential Dumping [T1003]: OS credential dumping typically occurs after access has already been gained. The most popular tool used by threat actors is Mimikatz, regardless of what group they may be associated with. There are several other tools that can accomplish the same goal of harvesting progressively more privileged account credentials. High-impact attacks require threat actors to compromise senior level administrative credentials.
Defense Evasion [TA0005]: Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Techniques used for defense evasion include uninstalling/disabling security software or obfuscating/encrypting data and scripts. Adversaries also leverage and abuse trusted processes to hide and masquerade their malware. Other tactics’ techniques are cross-listed here when those techniques include the added benefit of subverting defenses.
Indicator Removal on Host - Clear Windows Event Logs [T1070] involves 2 common event logs that get cleared by threat actors, Security and System. Security primarily records authentication, so if cleared, evidence of new account creations, remote access, or lateral movement can be lost. The System event log is helpful in identifying Service Installations, so if it’s cleared, evidence of any tools being used or stopping of services can be lost. This can be an effective way for a threat actor to cover some of their tracks.
Process Injection: Dynamic-link Library Injection [T1055] is when an actor injects their malware into a legitimate Windows process to try to avoid detection
Impair Defenses [T1562] is mainly the uninstallation or removal of antivirus software, or circumvention of anti-tampering configurations on EDR or detections software.
In Q4, there was a noticeable rotation away from attacks on the Professional Services sector. The Professional Services sector (small law firms, small financial service firms), has historically been the largest slice of the pie given the absolute volume of professional services firms, and the proportion of these firms that are under the cybersecurity poverty line. Professional service firms have historically made up ~20% of attacks. In Q4 that presentation shrunk to 10%. We attribute this subtle shift to threat actors targeting slightly larger mid-market companies where the probability of a large ransom is higher, vs. a very small professional service firm. Downtime days amongst all firms remained flat at 25% of disruption (note, this does not equate to 25 days of TOTAL disruption).