Fewer Ransomware Victims Pay, as Median Ransom Falls in Q2 2022
The cat and mouse game between ransomware affiliates and defenders spilled into new arenas of combat in Q2 of 2022. The looming question “What will happen once Conti disappears?” was answered rather quickly; nothing really changed except for name plates. The diaspora of Conti affiliates that was precipitated the Conti Leaks / Russian - Ukrainian invasion, were absorbed by existing and new Ransomware-as-a-Service (RaaS) groups such as Black Basta, BlackCat, Hive and Quantum.
Innovations in preventative policy evolved as two US States (Florida and North Carolina) banned municipal organizations from paying ransoms. Arguments from both sides of the debate weighed in, but the reality is that this is a worthy experiment and the data should be tracked very closely. The lack of uniform Blue Sky reporting may complicate analysis of if this policy is working vs. states that do not have similar laws.
However, The Cyber Incident Reporting Act, which provides mandatory incident reporting (a key element to data aggregation), was signed into law. The rule making and implementation time period means it may be 2+ years before the first report is filed with CISA. Expediting mandatory incident reporting would enable defenders to stay ahead of relentless cyber criminal innovation. Ransomware threat actors have been innovating as well. A year ago, a minority of ransomware variants were capable of encrypting non-Windows based operating systems. Today, almost ALL RaaS variants have stable Windows, Linux and ESXI versions and target every server, regardless of operating system.
Following the anniversaries of the Colonial pipeline and Kaseya attacks, defenders at large enterprises have had the opportunity to heavily invest in perimeter defense, privileged access management tools, segmentation, and continuity assets / strategies. These high profile attacks have enabled companies with ample security budgets and the right culture to make themselves very expensive targets for financially motivated attackers.
Ransomware affiliates seem to have become more leery of involving themselves, or their RaaS brand, in high profile attacks that could lead to increased geopolitical pressure and attention from law enforcement agencies. Following sharp law enforcement action against the DarkSide and Conti ransomware groups, RaaS operations have shifted in response. In particular, three key aspects of RaaS that were historically beneficial, may now harm RaaS operations:
RaaS Branding
Previously an asset: A name brand RaaS used to benefit affiliates. A strong brand could carry a reputation for cleanly decrypting the files of victims that paid and a leak site that punished non paying victims. This was a net positive for financially motivated affiliates.
Now a potential liability: Brands make attribution easier, and all it takes is one high profile attack on a pipeline or hospital to foul the brand and draw geopolitical or law enforcement attention.
Result: RaaS groups are keeping a lower profile and vetting affiilaites and their victims more thoroughly. More RaaS groups have formed, resulting in less concentration among the top few variants. Affiliates are frequently shifting between RaaS variants on different attacks, making attribution beyond the variant more challenging.
RaaS Infrastructure
Previously an asset: The back-end infrastructure that helped RaaS developers run their operations used to be a major asset as it enabled scale and increased profitability. If the back-end could be used for long periods of time, the return on the infrastructure investment accrued substantially.
Now a potential liability: Dependency upon sophisticated back-end infrastructures create larger attack surfaces. This increased the risk profile for ransomware developers as their digital footprint became more expensive and difficult to maintain and protect.
Result: RaaS groups are forced to invest more in the obfuscation and redundancy of their infrastructure, which decreases profit margins. It also limits available resources that could be used for innovation and expansion.
RaaS Shared Services
Previously an asset: RaaS operations used to assist affiliates by seeding initial access (via partnerships with botnets and access brokers), assisting with stolen data storage, centrally managing negotiations, and handling support via leak sites and decryptors.
Now a potential liability: All of the shared services had to be run by an expanding network of RaaS employees. The Conti leaks demonstrated that large shared service labor pools expose RaaS groups to moles, traitors, and systemic collapse.
Result: RaaS groups have ceased offering some of these shared services. In many cases, initial access is the responsibility of the individual affiliate. Stolen data storage and negotiations were also left to the affiliate.
The resulting environment is one where sophisticated RaaS affiliates are fluid, regularly moving between variants, or engaging in attacks with no branded malware. Attribution has always been hard, but it's getting harder in today's environment.
Average and Median Ransom Payment in Q2 2022
Average Ransom Payment
+8% from Q1 2022
Median Ransom Payment
-51% from Q1 2022
The average ransom payment increased +8% from Q1 2022 to $228,125. While the average was pulled up by several outliers, the median ransom payment actually decreased to $36,360, a 51% decrease from Q1 2022. This trend reflects the shift of RaaS affiliates and developers towards the mid market where the risk to reward profile of attack is more consistent and less risky than high profile attacks. We have also seen an encouraging trend among large organizations refusing to consider negotiations when ransomware groups demand impossibly high ransom amounts.
Data Exfiltration Remains Prevalent in Cyber Extortion
86% of ransomware cases involve a threat of leaking exfiltrated data. The proportion of companies that succumb to data exfiltration extortion continues to confound and frustrate Coveware and the IR industry at large. During Q2, we saw continued evidence that threat actors do not honor their word as it relates to destroying exfiltrated data. Despite our guidance, victims of data exfiltration continue to fuel the cyber extortion economy with these fruitless ransom payments. We will not change our messaging, and are encouraged that more private and public industry groups are pushing back against ransom payments for data exfiltration.
Recently, the UK’s National Cyber Security Centre and the Information Commissioner’s Office issued a joint letter, urging the legal community to closely evaluate the guidance provided to victims of data exfiltration extortion. In their letter they flatly state that, “[the] ICO does not consider the payment of monies to criminals who have attacked a system as mitigating the risk to individuals…”
Below are four common reasons victims cite when justifying payment for the suppression of exfiltrated data and our reasons why these are misguided:
Paying mitigates risk of harm to impacted parties: This is false. The moment data is stolen from a network the victim of the attack has likely accrued liabilities. These can include a federal, state or regulatory obligation to report the data breach. The victim company may have an obligation to pay for credit protection for impacted parties and to notify them of the data that was stolen. We make this point because these liabilities and obligations are present regardless of whether a cybercriminal posts the stolen data somewhere or not. The visibility of where stolen data is held or posted does not change the liabilities, and almost never changes the actual risk or harm to the impacted parties. If the stolen data has value to other cyber criminals, it will likely be sold out of view. Paying a ransom does not mitigate the risk or harm, or any liability the victim has to try to protect impacted parties.
Paying mitigates the potential for class action liability: There is no case law to support this. Most victims of data exfiltration do not fall into the category of even being at risk of a class action suit, as the number of impacted parties is not large enough. Even for companies that may be at risk, the reality is class action attorneys are going to attempt to bring a suit regardless, and that suit is likely to be settled out of court. Most of the suits are meritless, and are brought purely to perpetuate the class action legal profession. Paying a ransom is not going to thwart a meritless lawsuit, and there has been no case law to suggest that the the risk of a suit happening, or the resulting settlements or damages are mitigated by paying a ransom.
Paying shows my impacted parties that “we did everything to protect their data.”: Nope. This may sting to read, but if you are a victim of data exfiltration, the fact that data was successfully stolen directly contradicts this thesis. These incidents are preventable. They are not acts of god or mother nature. You did not do everything to prevent it. That is OK though. Doing everything to prevent it may not be possible for some of these attacks. It happened, and it’s happened to thousands of other companies. You are not alone. What matters is that you respect the intelligence of the impacted parties when you disclose the incident to them. If you approach impacted parties with the narrative of “this happened, but don’t worry, we paid to get the word of a cyber criminal that your data is now safe...” you are essentially messaging your constituents that one of your organization’s security policies is trusting the word of cyber criminals. We are not marketing or PR specialists over here, but we know most companies can do better than that. A far better narrative is to be candid, honest and contrite. Your impacted constituents will understand that this happens, and will appreciate the transparency. You won’t be the first counter-party to report a breach to a valued customer, and you won’t be the last. Disclosing a breach has never bankrupted a company. The sun will rise tomorrow….we promise.
Paying will limit brand damage from negative PR: Again, not likely. The PR wave that occurs when cyber criminals leak previously stolen data has a media half-life of about 6 hours. It is typically a flash in the pan. That flash in the pan can be further curtailed if data exfiltration victims set the narrative themselves. When victims pre-empt the media with their own press releases (i.e. create the scoop with their words, not a cyber criminal’s), the story becomes a non-story. These attacks happen every day. The media is burnt out reporting on them. When the narrative is set from the onset by the company, there is very little to report on, even if a cyber criminal posts the stolen data somewhere public. Additionally, once the PR wave has happened, the threats by the cyber criminal to cause damage via their posting are effectively de-fanged.
We don’t expect companies to always act in the best interest of society. For profit companies are aligned around shareholder value. This being said, when considering the points above, we hope future victims realize how frivolous these data exfiltration suppression payments are, especially given that the proceeds of these payments will be used to fund future attacks. These future attacks may have REAL disruptive consequences, such as attacks on hospitals or critical infrastructure. Victims of data exfiltration-only attacks can be part of the solution, by not paying.
Most Commonly Observed Ransomware Variants in Q2 2022
| Rank | Ransomware Type | Market Share % | Change in Ranking from Q1 2022 |
|---|---|---|---|
| 1 | BlackCat | 16.9% | +2 |
| 2 | Lockbit 2.0 | 13.1% | - |
| 3 | Hive | 6.3% | +1 |
| 4 | Quantum | 5.6% | New in Top Variants |
| 4 | Conti V2 | 5.6% | -3 |
| 5 | Phobos | 5% | +2 |
| 5 | Black Basta | 5% | New in Top Variants |
| 5 | AvosLocker | 5% | - |
Market Share of the Ransomware attacks
The collapse of the Conti RaaS operations and resulting affiliate diaspora has led to the growth and expansion of several existing and new RaaS operations. We expect that affiliates will continue to venue shop and hold multiple affiliations as a means of personal operational security. While some RaaS developers are still aiming for large market share, growth may be inhibited by the behavior of their own affiliates that prefer to spread their attacks across multiple brands.
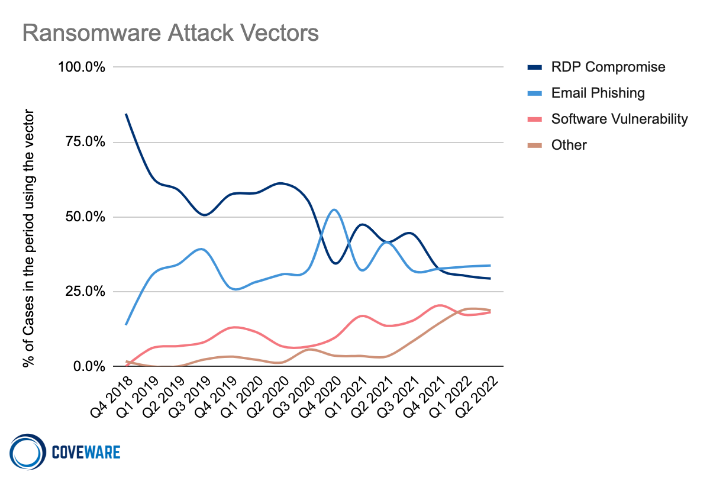
Ransomware Attack Vectors and MITRE ATT&CK TTPs Observed in Q2 2022
Initial Access: [TA0001]
Prevalent RaaS brands have decoupled from initial ingress botnets (like Trickbot & Emotet). This decrease in ‘shared’ ingress services has made observed attack vectors more diffuse and less correlative. We characterize the RaaS affiliate behavior of using what is immediately effective, affordable and available as affiliates ‘living off the land,’ as opposed to limiting themselves to one particular method of gaining initial access. This further complicates the attribution process as there are few ‘favorites’ for gaining initial access.
Below we have explained three of the top 5 MITRE ATT&CK tactics observed. Suggested detection and mitigations can be found by following the links.
Lateral Movement [TA0008]: Lateral Movement by threat actors consists of techniques used to enter and control remote systems on a network. Successful ransomware attacks require exploring the network to find key assets such as domain controllers, file share servers, databases, and continuity assets that are not properly segmented. Reaching these assets often involves pivoting through multiple systems and accounts to gain access. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier and harder to track. The 3 most observed forms of lateral movement are:
Remote Services [T1021], which is primarily the use of VNC (like TightVNC) to allow remote access or SMB/Windows Admin Shares. Admin Shares are an easy way to share/access tools and malware. These are hidden from users and are only accessible to Administrators. Threat actors using Cobalt Strike almost always place it in an Admin share.
Exploitation of Remote Services [T1210] - mainly consists of abusing internal remote desktop (RDP) after initial access has been made. Internal RDP is the quickest method for a threat actor to move from host to host, especially if they already have domain administrator credentials.
Lateral Tool transfer [T1570] primarily correlates to the use of PSexec, which is a legitimate windows administrative tool. Threat actors leverage this tool to move laterally or to mass deploy malware across multiple machines.
Discovery [TA0007]: Threat actors use Discovery techniques to gain knowledge about a target’s internal network. These techniques help adversaries observe the environment and orient themselves before deciding how to navigate the network to achieve their impact objectives. Native operating system tools are often used toward this post-compromise information-gathering objective.The three most observed tactics of discovery we observed in Q2 where:
Network Service Scanning (T1046) primarily consists of abusing Advanced IP Scanners to identify what network hosts are available.
Process Discovery (T1057) tools commonly abused are Process Explorer or Process Hacker, which allow threat actors to check active processes and kill them.
System Owner/User Discovery (T1033) is a tactic used to get a listing of accounts on a system or network. A common tool is Bloodhound.
Exfiltration [TA0010]: Exfiltration consists of techniques that threat actors may use to steal data from a network. Once data is internally staged, threat actors often package it to avoid detection while exfiltrating it from the bounds of a network. This can include compression and encryption. Techniques for getting data out of a target network typically include transferring stolen data over threat actor command and control channels. It may also include Exfiltration over Web Service [T1567] via use of a variety of third party tools such as megasync, rclone, Filezilla or Windows Secure Copy.
Common Industries Impacted by Ransomware in Q2 2022
Most Ransomware actors are industry agnostic, preferring to target companies that are economically favorable to attack, regardless of industry. This being said, some RaaS groups will avoid certain industries, such as certain health care organizations (like hospitals). In Q2, we observed subtle shifts as Health Care increased slightly, likely the result of Hive Ransomware expanding their attacks (Hive is indifferent to patient care and will attack hospitals without hesitation).
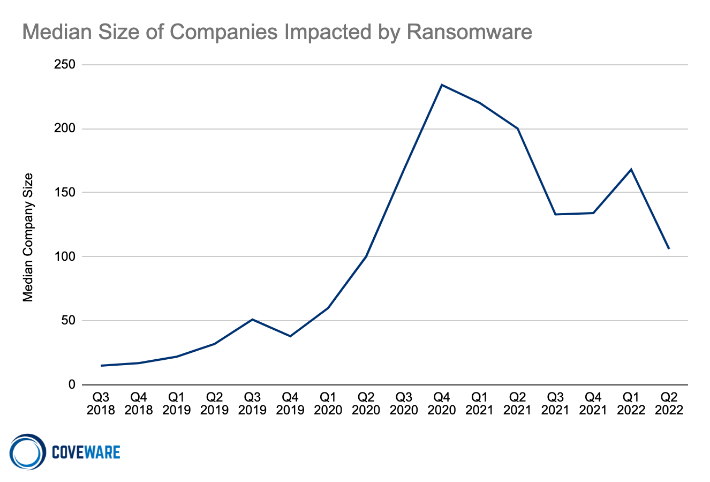
Average and Median Size of Companies Impacted by Ransomware in Q2 2022
While large enterprises continue to be impacted and certainly absorb the bulk of media coverage, Ransomware remains disproportionately a small-medium sized business problem. Small and medium sized businesses are more likely to under invest in cybersecurity, and make themselves very inexpensive targets for RaaS affiliates.
Downtime from Ransomware Attacks in Q2 2022
In Q2, the average days of downtime was measured at 24 days, a decrease of 8% from Q1 2022. This is due to the higher prevalence of attacks that only involved data exfiltration. Unlike encryption attacks which can completely disrupt business operations, data exfiltration-only attacks are much less disruptive to day to day operations, and cause less actual downtime that may cause material damage to a victim’s business.