Ransomware Amounts Rise 3x in Q2 as Ryuk & Sodinokibi Spread
NOTICE: We have been made aware that links to this blog post have been used by certain threat actors as advertisements, meant to legitimize or coerce victims into paying. We have notified law enforcement of this issue, and in no way do we condone the use of our data by criminals. DO NOT TRUST THE WORD OF CYBER CRIMINALS. As we note in our About Us page, use of our data by criminals is an unintended byproduct of our philosophy towards data transparency. Please Contact us if you have concerns or questions.
—
The Q2 Ransomware Marketplace report aggregates anonymized ransomware data from cases handled and resolved by Coveware’s Incident Response Team, and other Incident Response firms that utilize the Coveware Incident Response Platform to manage their own cases. Unlike surveys, which rely on sentiment, this report is solely created from a standardized set of data collected from every case. By aggregating and sharing this data we believe large and small enterprises can better protect themselves from the persistent and ever-evolving ransomware threat. Please don’t hesitate to reach out to us with any questions or comments. Thank you for reading!
How Much Does a Ransomware Attack Cost?
The total cost of a ransomware attack can be divided into two main costs. First, the recovery cost. These expenses cover forensic reviews and assistance in rebuilding servers and work stations. If a ransom is paid, then that is also a recovery expense. The second, and often more expensive cost of a ransomware attack is the total cost of downtime. Downtime costs are typically 5-10x the actual ransom amount and are measured in lost productivity (slack labor and lost revenue opportunities).
What Is the Average Ransom Payment?
In Q2 of 2019, the average ransom payment increased by 184% to $36,295, as compared to $12,762 in Q1 of 2019. The increase reflects the growing prevalence of Ryuk and Sodinokibi, variants of ransomware that have rapidly increased their demands. These types of ransomware are predominantly used in targeted attacks on larger enterprises, or on distributed networks of company’s via IT managed service providers or hosting ISPs.
Ransomware amounts paid daily during Q2 2019
How Much Downtime Does a Ransomware Attack Cause?
In Q2 of 2019 average downtime increased to 9.6 days, from 7.3 days in Q1 of 2019. The increase in downtime was primarily driven by the rise of Sodinokibi cases that targeted IT managed service providers (MSP) and their entire clientele base. In these cases, every end client of the MSP was impacted, which greatly magnified the impact of the attack and the time necessary to draw the incident to a resolution. Incident duration also increased for Phobos Ransomware cases. Phobos is ransomware as a service, and the current cohort of criminal affiliates are less organized and professional than others. This has led to protracted negotiations and a myriad of complications that can arise during decryption.
Average number of days of downtime sustained by victims of ransomware in Q2 2019
How Much Data Is Recovered After Paying a Ransom?
When a ransomware victim is forced to pay a ransom, there are two success metrics that determine the outcome. First, does the payment result in a working decryption tool being delivered? If the threat actor did not deliver, it is considered a default and will likely lead to a 0% data recovery rate. Second, if a working decryption tool is delivered, how effective is it in decrypting the data? Files and servers can be damaged during or after the encryption process and this can affect data recovery rates even when a decryptor tool is delivered.
How Often Is a Decryption Tool Delivered After Paying a Ransom?
In Q2 of 2019, 96% of companies that paid the ransom received a working decryption tool. This was the same as Q1 of 2019. Payment success rates do vary across different types of ransomware and different threat actor groups. For instance, Ryuk Ransomware has a 0% payment default rate. The groups distributing Ryuk typically deliver the decryptor tool within 2-3 hours of payment, with much reliability. Similarly, Sodinokibi’s use of an automated TOR site bolsters its reliability, and it also has a 0% payment default rate.
How Much Data Is Decrypted with a Ransomware Decryptor?
In Q2 2019, victims who paid for a decryptor recovered 92% of their encrypted data. This statistic varied dramatically depending on the ransomware type. For example, Ryuk ransomware has a relatively low data recovery rate, at ~87%. Data loss is typically a result of a flawed encryption process where files are partially encrypted or wiped. Variants such as Sodinokibi can also destroy file permissions, substantially delaying recovery times. Some clients reduce the expense of running inefficient decryptor tools and simply archive non-essential encrypted data for a rainy day.
What Cryptocurrencies Are Used to Pay for Ransomware?
Bitcoin is the dominant cryptocurrency used for ransomware payments. The depth and breadth of the bitcoin trading services make it the preferred medium of exchange for cyber extortion. We don’t expect other cryptocurrencies to gain share anytime soon, but it’s worth noting the role that privacy coins play in the cash out process.
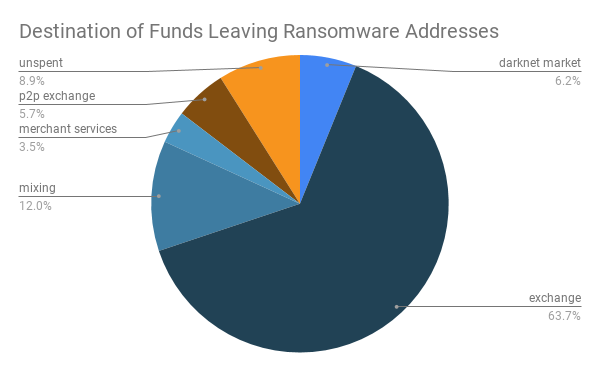
The below chart (supplied by blockchain compliance firm Chainalysis) shows the end destination of funds leaving wallets associated with ransomware payments. Almost 64% of ransomware proceeds are sent to exchanges. Once sent to an exchange, the bitcoin is swapped into privacy coins, further obfuscating the movement of illicit funds.
What Are the Most Common Types of Ransomware?
In Q2 2019, Ryuk became the most prevalent type of ransomware impacting enterprises. Ryuk has made a dramatic rise given it was not in the top 10 a year ago. Dharma & Phobos continue to make up a large portion of small enterprise incidents. Other notable changes where the retirement of GandCrab, and the rise of Sodinokibi in its place. Sodinokibi represents a major threat and appears to be the Ransomware-as-a-service of choice at the moment.
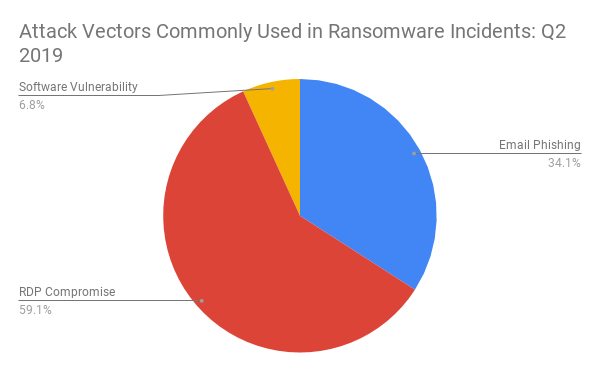
What Were the Most Commonly Identified Attack Vectors for Ransomware?
Email phishing continues to grow as a means to precipitate a ransomware attack, especially in larger enterprises. During the quarter, we observed phishing campaigns that ranged from highly generic, to exceptionally targeted and bespoke. Security awareness training continues to be a high ROI investment for larger enterprises that wish to curtail this risk. Remote Desktop Protocol (RDP) continues to be the most commonly identified attack vector, though it is primarily effective on smaller enterprises.
Comparing the Top Three Types of Ransomware by Attack Vector
Ransomware attack patterns are extremely common from case to case. Attackers target the cheapest and easiest to exploit the vulnerability. The attack vectors vary by ransomware type as the personality, specialized expertise and victim profile can vary from group to group. Ryuk ransomware groups tend to target larger organizations. Large organizations typically have good patch management programs and large IT security teams. Penetrating large enterprises via software vulnerabilities or misconfigured remote access ports is difficult. Accordingly, Ryuk groups target the softest part of these large enterprises, their employees, via phishing emails. On the other end of the spectrum, Ransomware-as-a-service Sodinokibi has been targeting IT managed service providers through a variety of software vulnerabilities. The vulnerabilities allow the attacker to take control of the service providers management tools and push their ransomware to every endpoint managed. Some common vulnerabilities spotted during the quarter were:
CVE-2017-18362: This vulnerability in the Connectwise/Kaseya integration gives the attacker unauthenticated remote commands to the VSA database.
Webroot 2FA: This common MSP tool was exploited multiple times during the quarter, prompting the manufacturer to force 2FA upon its entire user base.
Comparing the Top Three Types of Ransomware by the Size of the Victim Company
The Q2 data paints a dramatic picture. Ryuk ransomware is clearly targeting large enterprises, while Dharma and Sodinokibi target small and medium-size organization. There are less common ransomware variants that have similar target patterns.
Comparing the Top Three Types of Ransomware by Ransom Amount
Ryuk continues to be the most expensive type of ransomware by an order of magnitude. However, the average Ryuk ransom amount actually fell slightly between Q1 and Q2 reflecting the broadening focus of targets that the group is aiming for. During the quarter large multinational companies were targeted alongside small local medical practices. Sodinokibi attacks ramped up their activity via mass proliferation by targeting lots of small businesses simultaneously via a single managed service provider. These attacks can be devastating to the company and service provider alike and often takes weeks to resolve.
What Industries Are Commonly Targeted by Ransomware?
Public sector organizations accounted for about 3% of incidents during Q2, though they seemed to garner 100% of media attention. It’s worth noting that public sector victims paid an average ransom of $338,700, almost 10x the global enterprise average. The rise of Sodinokibi has also put managed service providers squarely in the crosshairs of ransomware distributors. Sodinokibi highlights how threat actors are increasing the magnitude of their attacks by using a single IT service provider’s vulnerability to impact their entire clientele base.
What Was the Average Size of Company Targeted by Ransomware?
In Q2 of 2019, the average company size increased to 925 employees, up from 114 in Q1. This rise reflected an increased prevalence of ransomware types that target large enterprises, such as Ryuk.
Disclaimer:
Coveware is not responsible for any actions taken, errors or omissions (negligent or otherwise), regardless of the cause, or for the results obtained from the use of this content, or for the performance of any computer, hardware or software used or modified in conjunction with this content. The content is provided on an "as is" basis.
VIEWERS OF THIS REPORT AND ITS CONTENT DISCLAIM ANY AND ALL EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, ANY WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE OR USE, FREEDOM FROM BUGS, SOFTWARE ERRORS OR DEFECTS, THAT THE CONTENT'S FUNCTIONING WILL BE UNINTERRUPTED OR THAT THE CONTENT WILL OPERATE WITH ANY SOFTWARE OR HARDWARE CONFIGURATION.
In no event shall Coveware be liable to any party for any direct, indirect, incidental, exemplary, compensatory, punitive, special or consequential damages, costs, expenses, legal fees, or losses (including, without limitation, lost income or lost profits and opportunity costs or losses caused by negligence) in connection with any use of the content even if advised of the possibility of such damages.
Some images designed by ITIM2010 from Flaticon