Coveware's 2018 Q4 Ransomware Marketplace Report
Today we released our Q4 Global Ransomware Marketplace Report. In this report, we aggregated data points collected from cases handled during the prior quarter and highlight the trends we have observed. We released this information believing that aggregating hard data points from ransomware incidents will shine a light on how these attacks occur and prevent future attacks. Anonymized segments of our data are routinely provided to law enforcement agencies to augment efforts to identify and apprehend perpetrators of attacks. Additionally, we are excited to share our data with the No More Ransomware organization and its diverse group of contributing partner organizations. Below are some key trends we observed in Q4 of 2018.
What was the Average Ransomware Ransom Amount?
The average ransom increased by 13% as compared to Q3 of 2018 ($5,973). Coveware suspects the increase reflects the more targeted nature of recent ransomware attacks. In Q4, ransomware distributors focused on larger targets and via bespoke RDP & social engineering attack vectors. Higher priced ransomware strains like SamSam and Ryuk also increased in frequency during Q4, despite the ubiquity of Dharma, GandCrab and Globelmposter.
How Much Downtime does a Ransomware Incident Cause?
Average downtime increased by 47% over Q3, also reflecting the increasingly bespoke nature of the attacks. The increase in downtime was due to the frequency of attacks where backup systems were wiped or encrypted as part of the attack. We estimated downtime costs by reviewing the location and the industry of the organization and using labor and margin statistics to estimated downtime costs per hour.
What Cryptocurrencies are used in Ransomware?
Bitcoin, despite its falling price in Q4, continues to be the preferred cryptocurrency for ransomware. While Bitcoin wallets are anonymous, the transactions are trackable. Gandcrab charges 10% more for ransomware if paid in Bitcoin vs Dash, which is known for its greater anonymity.
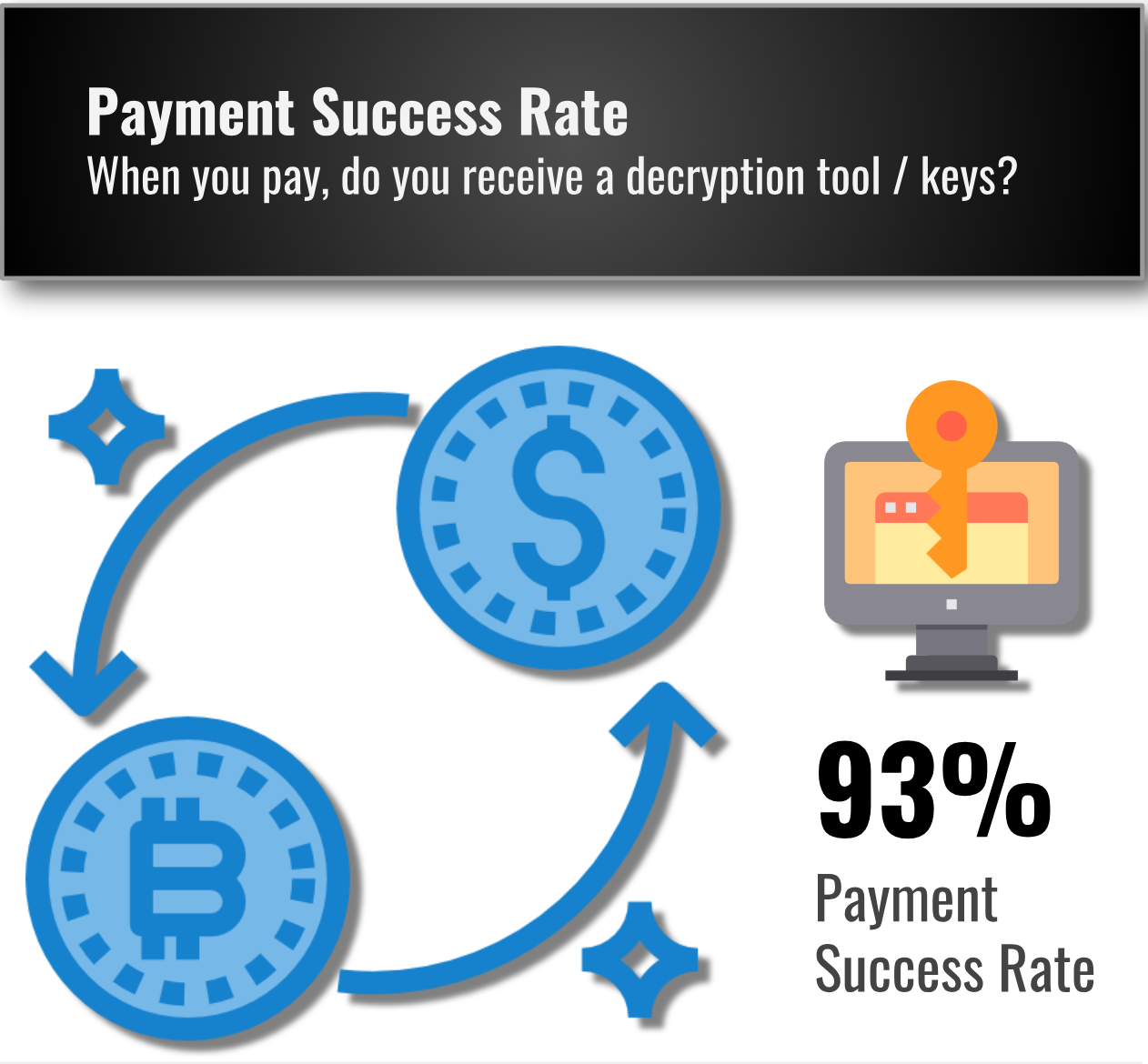
When you Pay Ransomware, do you Receive a Decryptor Tool?
93% of the time, paying the ransom results in a decryption tool. However, payment success rates vary dramatically based on ransomware type, and the victim company’s negotiation and payment tactics. For example, the GandCrab TOR site is very reliable and delivers a decryptor tool if you pay. However, some variants of Dharma can be much riskier depending on the variant and individual distributor.
What is the Overall Data Recovery Rate when Ransomware is Paid?
When a victim of ransomware pays, they receive a decryption key 93% of the time, but that is just the beginning of the recovery process. Encryption can damage or wipe files, and sometimes the decryption tools do not work well. The average data recovery rate when a working tool is delivered is about 95% but varies dramatically depending on the type of ransomware. For example, Ryuk is low at ~60%, while SamSam is close to 100%.
What are the Most Common type of Ransomware?
Dharma/Crysis was the most prevalent type of ransomware in Q4. Distribution and variants increased significantly as did payment defaults. Dharma extensions .adobe and .gamma were the worst offenders registering the most payment defaults out of any other ransomware type. We attribute this to the increased syndication to less sophisticated ransomware distributors during the quarter.
What are the Top Ransomware Attack Vectors
Remote Desktop Protocol (RDP) based breaches were AGAIN the most prevalent ransomware attack vector in Q4. Accordingly, ransomware distributors are spending increased time inside of breached networks. Admin credentials are harvested so backups can be wiped or encrypted, ensuring the attack has maximum impact. We expect this attack vector to remain popular until the number of vulnerable targets shrinks.
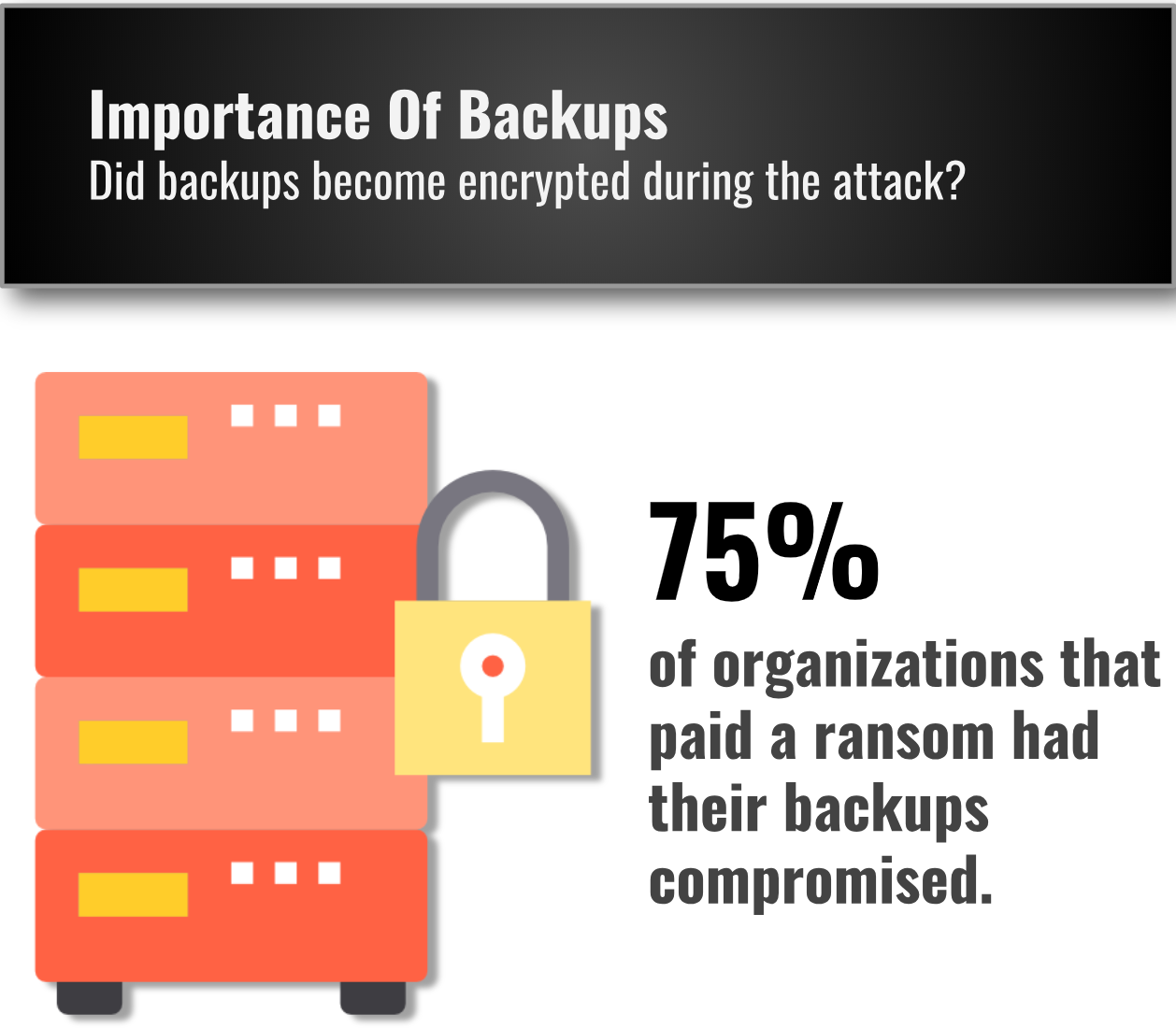
How often are Backups Encrypted or Wiped by a Ransomware Attack?
The percentage of companies with compromised backups increased over 54% in Q3. This is consistent with the increasingly bespoke nature of ransomware attacks in Q4. Backup systems are typically the first target of the hacker. Next, hackers encrypt the primary file and application servers in order to completely cripple the target company. Proper network partitioning and ‘least privilege’ administrative access are a must to avoid being compromised.
What Industries are Most Targeted by Ransomware?
Professional service firms, such as regional law firms and CPA firms, continue to be a prime target for ransomware. These firms tend to under-invest in IT security, have weak or no backup policies, and have almost no tolerance for data loss. We also observed an increase in local healthcare facilities being targeted. These attacks typically caused the facility to close their doors until critical scheduling and patient EMR servers could be recovered.
What is the Average size of a Company Attacked by Ransomware?
The average company size doubled to over 70 employees in Q4, up from 38 in Q3. This statistic compliments our observation that ransomware is becoming increasingly bespoke, targeting larger companies with more targeted attacks, and demanding higher ransoms.
What type of IT do Organizations that get Attacked Typically Employee?
Ransomware attacks moved up market in Q4, and accordingly the profile of the victim company’s IT staff shifted towards in-house, rather than outsourced. Outsourced MSPs (Managed Service Providers) continued to be tested as both end clients, and break fix clients become targets.
Do Organizations Increase IT Security Spending following a Ransomware Attack?
The percentage of companies that planned to increase their IT security spend following a ransomware attack increased in Q4. This likely reflects the larger profile of the average company and their ability to allocate budget to IT security spending.
Securing Remote Access Has Never Been More Important
Ransomware distributors shifted away from malicious email attachments and now overwhelmingly exploit RDP as the preferred attack vector. A typical ransomware campaign exploits RDP for initial access and then gains elevated credentials to move laterally within a network. The attacker typically used these credentials to wipe backups before planting ransomware on critical machines. 85% of ransomware attacks in Q4 exploited RDP as the primary attack vector. We expect this trend to hold as long as companies continue to have poorly secured RDP access.
Ransomware is Targeting Backups at an Alarming Rate
75% of our Q4 ransomware cases involved the wiping or encryption of primary and secondary backups (up from 54% in Q3). Backup systems that are non-partitioned, not protected by 2FA, or not air gapped from the network are low hanging fruit to an attacker with administrative credentials. The security necessary to defend against these types of attacks is increasingly sophisticated and is putting pressure on small businesses to invest in a comprehensive but prudent solution that includes endpoint, AV, ‘least privilege access’ and properly partitioned backups.
Ransomware is Targeting Larger Organizations in the Services Industries
Professional service organizations, such as regional law firms and CPA firms, are under increasing attack from ransomware. The average victim company size increased from 38 to 71 employees in Q4. On average these firms incurred over 6 days of complete or partial downtime. Mid-market companies, especially those in low gross margin industries, such as IT hosting or freight and logistics, are at grave risk of existentially risky downtime if they sustain an attack that causes customer level service interruption.
Popular Ransomware Types Remain, Ryuk and Bitpaymer are Traveling Down Market
For the second quarter in a row, Dharma remained the most common type of ransomware. Other widely distributed types of ransomware such as GandCrab and Globelmposter were also prevalent, but headlines were made as Ryuk and Bitpaymer began showing up in small business attacks. The appearance of these two very expensive types of ransomware down market is evidence that these strains are being more broadly distributed by the same groups that utilize other types of ransomware.